Over 37,000 internet-exposed VMware ESXi cases are at risk of CVE-2025-22224, a serious out-of-bounds write flaw this is actively exploited within the wild.
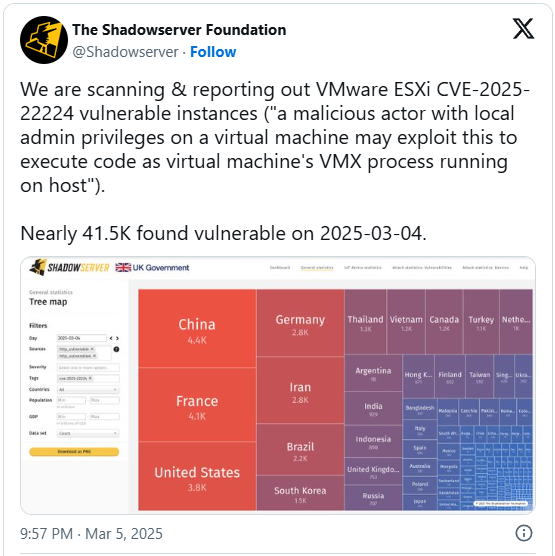
This large publicity is being reported through risk tracking platform The Shadowserver Basis, which reported a determine of round 41,500 the day past.
As of late, ShadowServer now reviews that 37,000 are nonetheless susceptible, indicating that 4,500 gadgets had been patched the day past.
CVE-2025-22224 is a critical-severity VCMI heap overflow vulnerability that allows native attackers with administrative privileges at the VM visitor to flee the sandbox and execute code at the host because the VMX procedure.
Broadcom warned consumers about it along side two different flaws, CVE-2025-22225 and CVE-2025-22226, on Tuesday, March 4, 2025, informing that each one 3 had been being exploited in assaults as zero-days.
The issues had been found out through Microsoft Risk Intelligence Heart, which noticed their exploitation as 0 days for an undisclosed length. Additionally, no details about the beginning of the assaults and the goals has been shared but.
The U.S. Cybersecurity & Infrastructure Safety Company (CISA) has given federal companies and state organizations till March 25, 2025, to use the to be had updates and mitigations or forestall the use of the product.
The Shadowserver Basis reviews that many of the susceptible cases are in China (4,400), adopted through France (4,100), america (3,800), Germany (2,800), Iran (2,800), and Brazil (2,200).
On the other hand, because of the standard use of VMware ESXi, a well-liked hypervisor used for virtualization in endeavor IT environments for digital system control, the have an effect on is world.
For more info at the ESXi variations that repair CVE-2025-22224, customers are beneficial to test Broadcom’s bulletin. Recently, there are not any workarounds for this downside.
The seller has additionally revealed a FAQ web page for customers to percentage further motion suggestions and have an effect on main points.
