Safety researchers at Bishop Fox have revealed entire exploitation main points for the CVE-2024-53704 vulnerability that permits bypassing the authentication mechanism in positive variations of the SonicOS SSLVPN software.
The seller warned concerning the top exploitation risk of the flaw in a bulletin on January 7, urging directors to improve their SonicOS firewalls’ firmware to handle the issue.
“Now we have known a firewall vulnerability this is prone to exact exploitation for patrons with SSL VPN or SSH control enabled, and that are supposed to be mitigated right away by means of upgrading to the most recent firmware,” warned SonicWall in an electronic mail despatched to consumers on the time.
The flaw lets in a far flung attacker to hijack lively SSL VPN classes with out authentication, granting them unauthorized get admission to to the sufferer’s community.
On January 22 Bishop Fox researchers introduced that that they had advanced an exploit for CVE-2024-53704 after a “vital reverse-engineering effort,” confirming SonicWall’s fears concerning the exploitation possible of the vulnerability.
Supply: Bishop Fox
After permitting a while for gadget directors to use the to be had patches, Bishop Fox launched the entire exploitation main points on Monday.
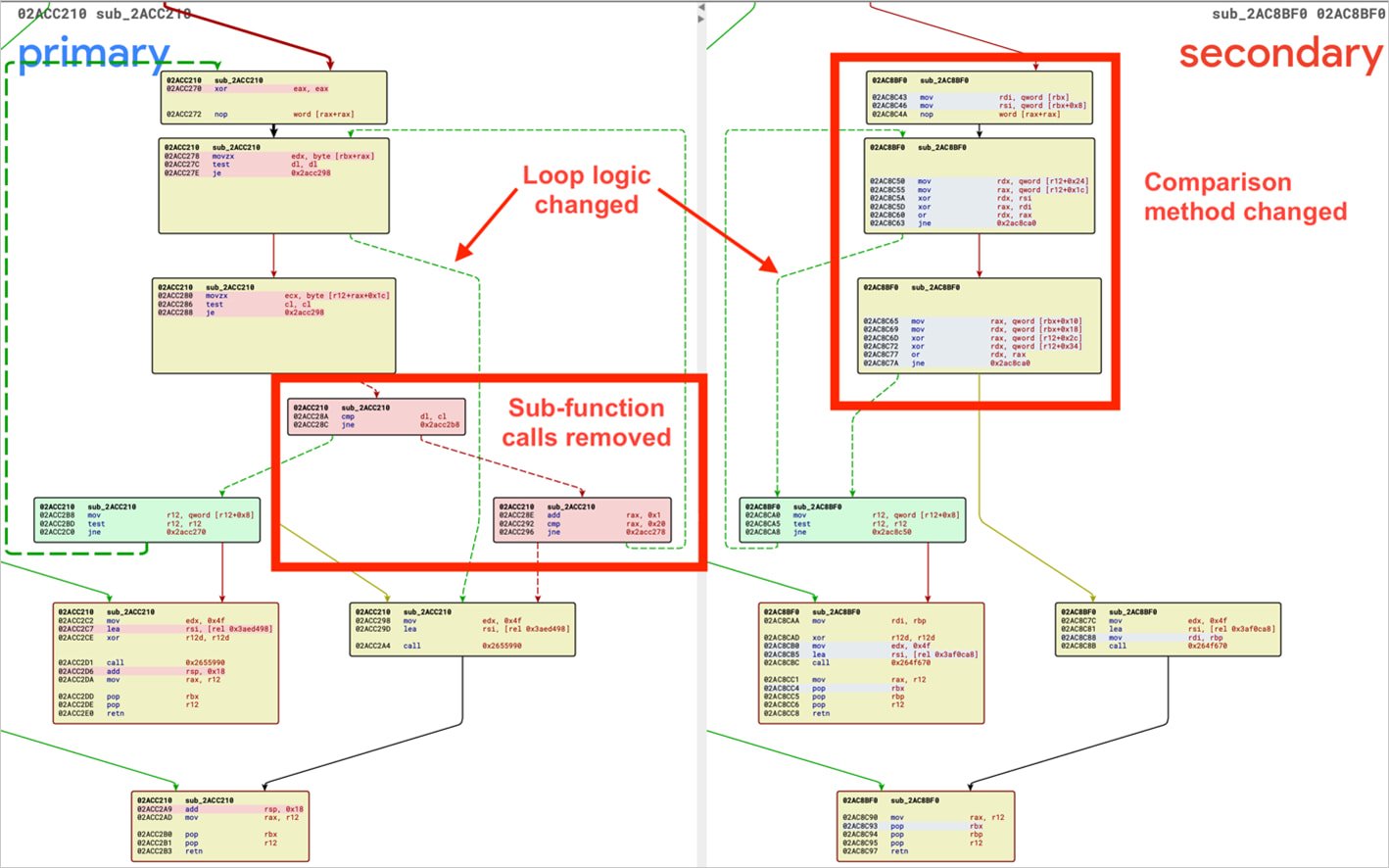
The exploit works by means of sending a specifically crafted consultation cookie containing a base64-encoded string of null bytes to the SSL VPN authentication endpoint at ‘/cgi-bin/sslvpnclient.’
This triggers an improper validation of the consultation, because the mechanism assumes that the request is related to an lively VPN consultation.
This logs out the sufferer and provides the attacker get admission to to the consultation, permitting them to learn the person’s Digital Workplace bookmarks, download VPN shopper configuration settings, open a VPN tunnel to the interior community, and gives get admission to to non-public community assets.
Supply: Bishop Fox
The researchers put the validity in their research to the take a look at and created a proof-of-concept exploit code to simulate an authentication bypass assault. The reaction headers confirmed that that they had effectively hijacked an lively consultation.
“With that, we had been in a position to spot the username and area of the hijacked consultation, along side personal routes the person used to be in a position to get admission to in the course of the SSL VPN,” the researchers stated.
Safety updates to be had
The problem affects SonicOS variations 7.1.x (as much as 7.1.1-7058), 7.1.2-7019, and eight.0.0-8035. Those variations run in more than one fashions of Gen 6 and Gen 7 firewalls, in addition to SOHO sequence units.
Fixes had been made to be had in SonicOS 8.0.0-8037 and later, 7.0.1-5165 and better, 7.1.3-7015 and better, and six.5.5.1-6n and better. For model-specific data, take a look at SonicWall’s bulletin right here.
Bishop Fox says that information superhighway scans as of February 7 display kind of 4,500 internet-exposed SonicWall SSL VPN servers with out the protection updates solving CVE-2024-53704.
With a running proof-of-concept exploit now publicly to be had, admins will have to practice the updates once conceivable since the exploitation possibility for CVE-2024-53704 has larger considerably.
