Hackers are launching assaults in opposition to Palo Alto Networks PAN-OS firewalls by way of exploiting a lately mounted vulnerability (CVE-2025-0108) that permits bypassing authentication.
The safety factor gained a high-severity rating and affects the PAN-OS control internet interface and permits an unauthenticated attacker at the community to circumvent authentication and invoke positive PHP scripts, probably compromising integrity and confidentiality.
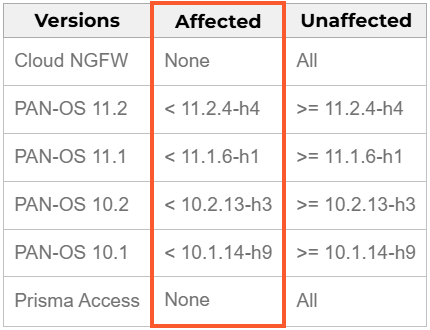
In a safety bulletin on February 12, Palo Alto Networks urges admins to improve firewalls to the variations under to handle the problem:
- 11.2.4-h4 or later
- 11.1.6-h1 or later
- 10.2.13-h3 or later
- 10.1.14-h9 or later
PAN-OS 11.0 may be impacted however the product reached the tip of lifestyles (EoL) and Palo Alto Networks does now not plan to unencumber any fixes for it. As a result of this, customers are strongly really useful to improve to a supported unencumber as an alternative.
Supply: Palo Alto Networks
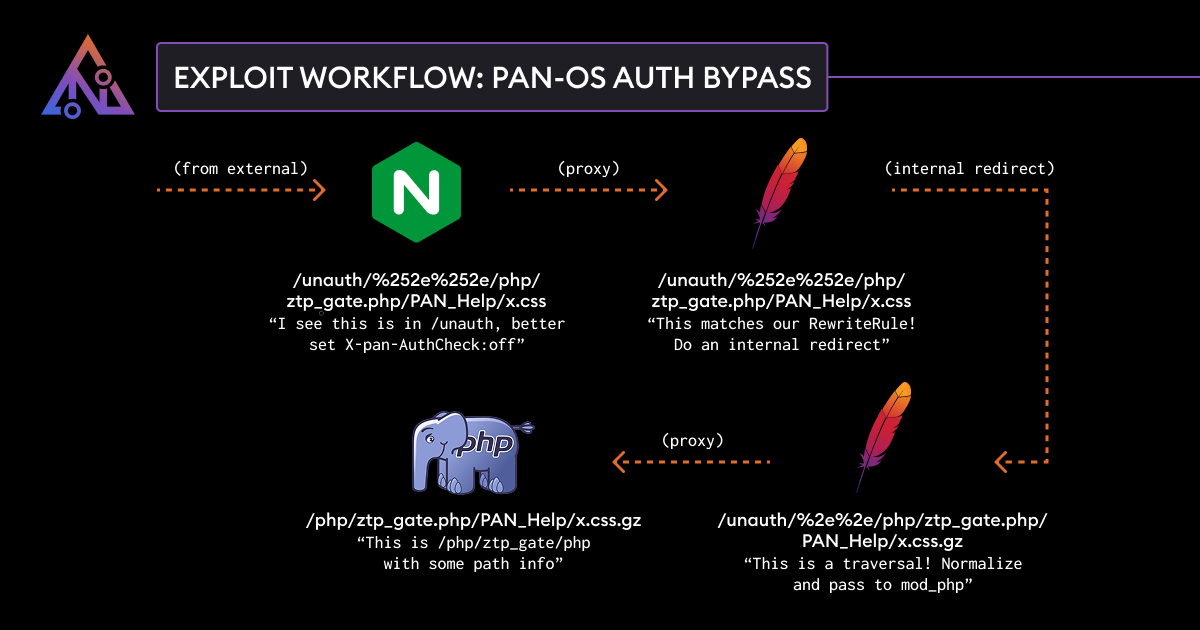
The vulnerability used to be found out and reported to Palo Alto Networks by way of safety researchers at Assetnote. Additionally they revealed a write-up with whole exploitation main points when the patch used to be launched.
The researchers demonstrated how the flaw might be leveraged to extract delicate machine knowledge, retrieve firewall configurations, or probably manipulate positive settings inside of PAN-OS.
The exploit leverages a trail confusion between Nginx and Apache in PAN-OS that permits bypassing authentication.
Attackers with community get entry to to the control interface can leverage this to assemble intelligence for additional assaults or to weaken safety defenses by way of editing available settings.
Supply: Assetnote
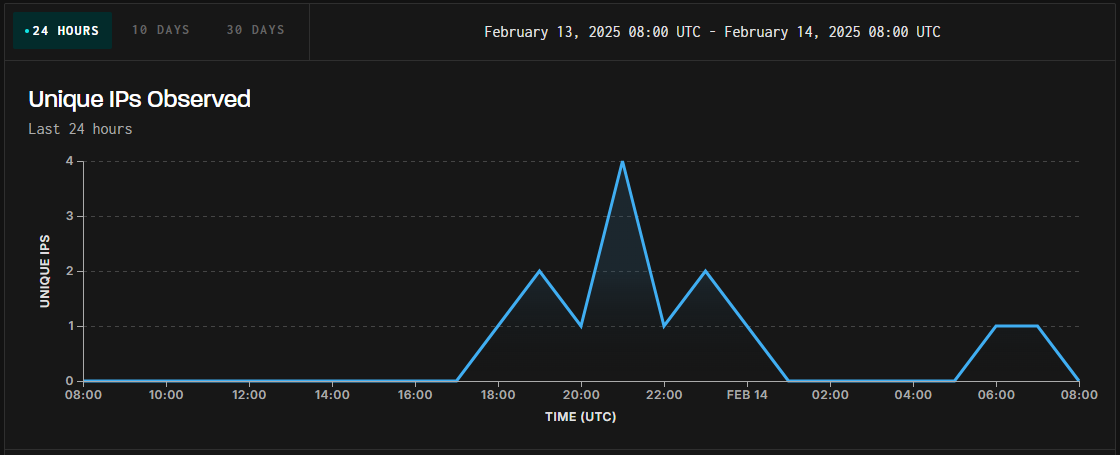
Risk tracking platform GreyNoise logged exploitation makes an attempt focused on unpatched PAN-OS firewalls.
The assaults began on February 13, at 17:00 UTC, and seem to originate from a number of IP addresses, probably indicating exploitation efforts from distinct risk actors.
Supply: GreyNoise
In regards to the publicity of prone units on-line, Macnica researcher Yutaka Sejiyama instructed BleepingComputer that there are these days over 4,400 PAN-OS units exposing their control interface on-line.
To protect in opposition to the continued exploitation process, which, making an allowance for that the PoC is public, may be very more likely to culminate within the following days, it is strongly recommended to use the to be had patches and limit get entry to to firewall control interfaces.
Replace 2/18 – Palo Alto Networks despatched BleepingComputer the under remark in regards to the process noticed within the wild.
“The safety of our consumers is our best precedence. Palo Alto Networks has showed studies of energetic exploitation focused on a vulnerability (CVE-2025-0108) within the PAN-OS internet control interface. This vulnerability, chained with different vulnerabilities like CVE-2024-9474, may just permit unauthorized get entry to to unpatched and unsecured firewalls.
We’re urging all consumers with internet-facing PAN-OS control interfaces to right away observe the safety updates launched on February 12, 2025. Securing external-facing control interfaces is a elementary safety very best follow, and we strongly inspire all organizations to study their configurations to attenuate chance.
Detailed data and mitigation steering are to be had within the CVE-2025-0108 safety advisory: https://safety.paloaltonetworks.com/CVE-2025-0108″
