Over 22,000 CyberPanel cases uncovered on-line to a vital far flung code execution (RCE) vulnerability have been mass-targeted in a PSAUX ransomware assault that took virtually all cases offline.
This week, safety researcher DreyAnd disclosed that CyberPanel 2.3.6 (and most likely 2.3.7) suffers from 3 distinct safety issues that can lead to an exploit permitting unauthenticated far flung root get admission to with out authentication.
Particularly, the researcher exposed the next issues on CyberPanel model 2.3.6:
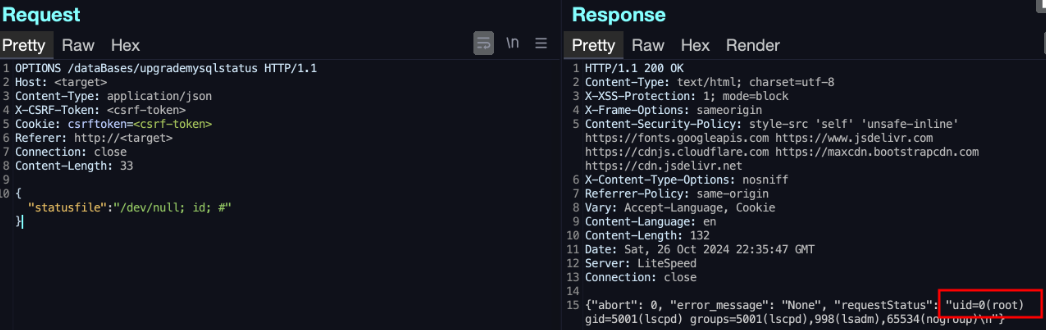
- Faulty authentication: CyberPanel tests for consumer authentication (login) on every web page one by one as a substitute of the use of a central device, leaving sure pages or routes, like ‘upgrademysqlstatus,’ unprotected from unauthorized get admission to.
- Command injection: Consumer inputs on unprotected pages aren’t correctly sanitized, enabling attackers to inject and execute arbitrary device instructions.
- Safety filter out bypass: The safety middleware simplest filters POST requests, permitting attackers to avoid it the use of different HTTP strategies, like OPTIONS or PUT.
Supply: DreyAnd
The researcher, DreyAnd, advanced a proof-of-concept exploit to reveal root-level far flung command execution at the server, permitting him to take whole keep watch over of the server.
DreyAnd advised BleepingComputer that he may just simplest take a look at the exploit on model 2.3.6 as he didn’t have get admission to to the two.3.7 model on the time. Then again, as 2.3.7 was once launched on September 19, ahead of the malicious program was once discovered, it was once most likely impacted as smartly.
The researcher stated they disclosed the flaw to the CyberPanel builders on October 23, 2024, and a repair for the authentication factor was once submitted later that night on GitHub.
Whilst any individual who installs CyberPanel from GitHub or in the course of the improve procedure gets the protection repair, the builders have now not launched a brand new model of the device or issued a CVE.
BleepingComputer has contacted CyberPanel to invite once they plan to unlock a brand new model or safety announcement, however we’re nonetheless expecting their reaction.
Focused in PSAUX ransomware assault
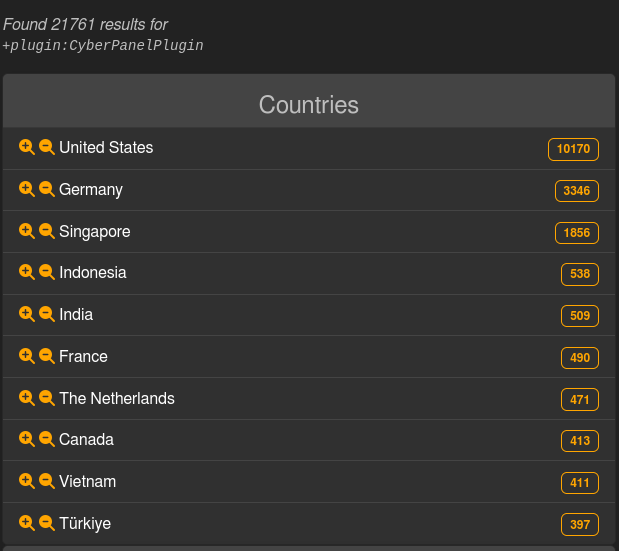
The day gone by, the risk intel seek engine LeakIX reported that 21,761 prone CyberPanel cases have been uncovered on-line, and just about part (10,170) have been in the USA.
Supply: LeakIX | X
Then again, in a single day, the choice of cases mysteriously dropped to just about 400 cases, with LeakIX telling BleepingComputer the impacted servers are now not available.
Cybersecurity researcher Gi7w0rm tweeted on X that those cases controlled over 152,000 domain names and databases, for which CyberPanel acted because the central get admission to and control device.
LeakIX has now advised BleepingComputer that risk actors mass-exploited the uncovered CyberPanel servers to put in the PSAUX ransomware.
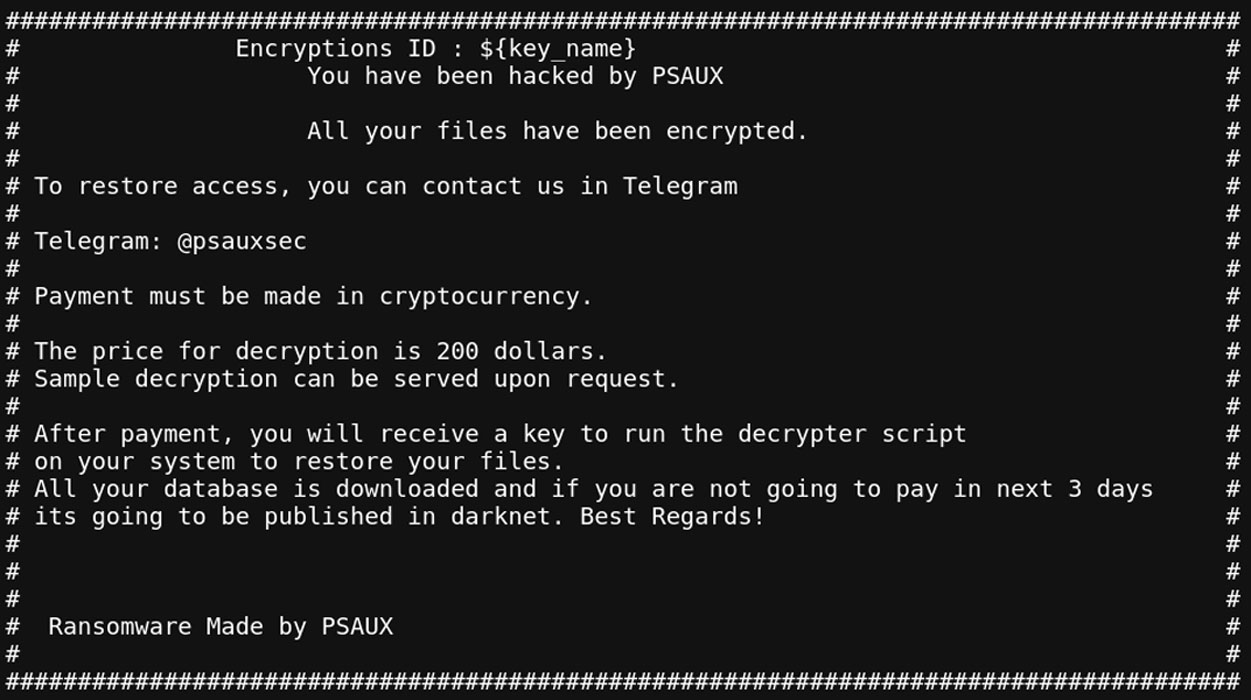
The PSAUX ransomware operation has been round since June 2024 and objectives uncovered internet servers via vulnerabilities and misconfigurations.
Supply: LeakIX
When introduced on a server, the ransomware will create a singular AES key and IV and use them to encrypt the information on a server.
The ransomware may even create ransom notes named index.html in each folder and replica the ransom word to /and so on/motd, so it’s proven when a consumer logs into the software.
When completed, the AES key and IV are encrypted the use of an enclosed RSA key and stored as /var/key.enc and /var/iv.enc.
LeakIX and Chocapikk received the scripts used on this assault, which come with an ak47.py script for exploiting the CyberPanel vulnerability and any other script named if truth be told.sh to encrypt the information.
Then again, a weak point has been discovered that can permit the decryption of information totally free, with researchers these days investigating if this is conceivable.
Because of the energetic exploitation of the CyberPanel flaw, customers are strongly instructed to improve to the most recent model on GitHub once conceivable.
Updte 10/29/24: LeakIX has launched a decryptor that can be utilized to decrypt information encrypted on this marketing campaign.
It will have to be famous that if the risk actor applied other encryption keys, then decrypting with the flawed one may just corrupt your knowledge.
Subsequently, you’ll want to make a backup of your knowledge ahead of making an attempt to make use of this decryptor to first take a look at that it really works.
