DrayTek has launched safety updates for more than one router fashions to handle 14 vulnerabilities of various severity, together with a far flung code execution flaw that won the utmost CVSS rating of 10.
The failings, which Forescout Analysis – Vedere Labs came upon, affect each actively supported and fashions that experience reached end-of-life. Alternatively, because of the severity, DrayTek has equipped fixes for routers in each classes.
The researchers warned that their scans printed that roughly 785,000 DrayTek routers may well be at risk of the newly came upon set of flaws, with over 704,500 having their internet interface uncovered to the web.
Vulnerability main points
Maximum vulnerabilities came upon through Vedere Labs are medium-severity buffer overflow and cross-site scripting issues dictated through a number of exploitation necessities.
Alternatively, 5 of the failings elevate important dangers, requiring rapid consideration. The ones are summarized as follows:
- FSCT-2024-0006: A buffer overflow vulnerability within the “GetCGI()” serve as, accountable for dealing with HTTP request information, which can result in denial of carrier (DoS) or far flung code execution (RCE). (CVSS rating: 10.0)
- FSCT-2024-0007: Command Injection in OS Verbal exchange – The “recvCmd” binary used for communique between the host and visitor working methods is at risk of command injection assaults, probably permitting VM break out. (CVSS rating: 9.1)
- FSCT-2024-0014: The internet server backend makes use of a static string to seed the pseudo-random quantity generator (PRNG) in OpenSSL for TLS connections, which might result in knowledge disclosure and man-in-the-middle (MiTM) assaults. (CVSS rating: 7.6)
- FSCT-2024-0001: The usage of similar admin credentials throughout all the device can result in complete device compromise if those credentials are bought. (CVSS rating: 7.5)
- FSCT-2024-0002: An HTML web page within the Internet UI improperly handles enter, making an allowance for mirrored XSS vulnerabilities. (CVSS rating: 7.5)
As of but, there were no stories of lively exploitation of those flaws, and the e-newsletter of analytical main points has been withheld to permit customers sufficient time to use the protection updates.
The above flaws affect 24 router fashions, of which 11 have reached the top of existence but nonetheless won fixes.
The impacted fashions and goal firmware variations to improve to may also be noticed within the desk beneath.
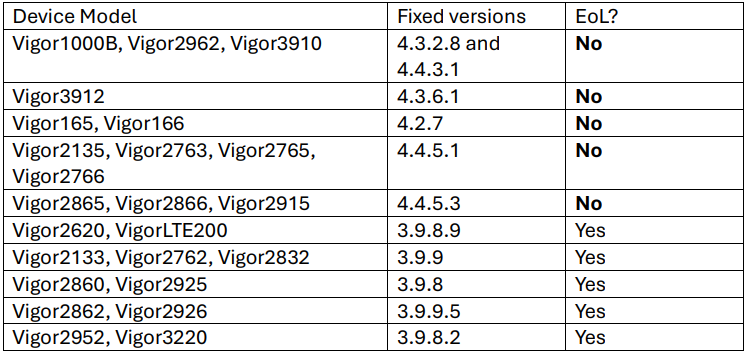
Customers might obtain the most recent firmware for his or her tool type from DrayTek’s reliable obtain portal.
Over 700,000 DrayTex gadgets uncovered on-line
Verdere Labs stories that it discovered over 704,500 gadgets have the DrayTek Vigor Internet person interface uncovered to the web, although it must handiest be available from an area community.
Just about part of the gadgets below Forescout’s direct visibility are positioned in america, however Shodan effects display important numbers in the UK, Vietnam, the Netherlands, and Australia.
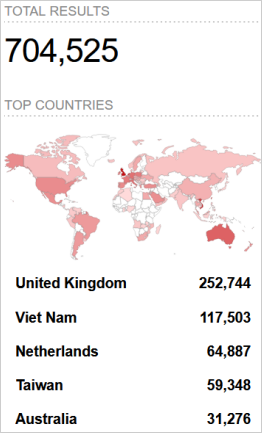
Supply: Verdere Labs
Except for making use of the most recent firmware updates, customers are advisable to take the next movements:
- Disable far flung get entry to if now not wanted, and use an get entry to regulate checklist and two-factor authentication when lively.
- Take a look at settings for arbitrary alterations or the addition of admin customers or far flung get entry to profiles.
- Disable SSL VPN connections via port 443.
- Permit syslog logging to watch for suspicious occasions.
- Permit auto-upgrade to HTTPs pages to your internet browser.
All DrayTek customers must ascertain that their tool’s far flung get entry to console is disabled, as exploits and brute power assaults recurrently goal the ones products and services.
