Risk actors are chaining in combination ServiceNow flaws the use of publicly to be had exploits to breach govt companies and personal corporations in knowledge robbery assaults.
This malicious job was once reported through Resecurity, which, after tracking it for per week, known more than one sufferers, together with govt companies, knowledge facilities, power suppliers, and instrument building corporations.
Even supposing the seller launched safety updates for the issues on July 10, 2024, tens of hundreds of programs doubtlessly stay at risk of assaults.
Exploitation main points
ServiceNow is a cloud-based platform that is helping organizations organize virtual workflows for endeavor operations.
It’s broadly followed throughout quite a lot of industries, together with public sector organizations, healthcare, monetary establishments, and big enterprises. FOFA cyber web scans go back just about 300,000 internet-exposed cases, reflecting the product’s reputation.
On July 10, 2024, ServiceNow made hotfixes to be had for CVE-2024-4879, a crucial (CVSS rating: 9.3) enter validation flaw enabling unauthenticated customers to accomplish far off code execution on more than one variations of the Now Platform.
The following day, on July 11, Assetnote researchers who found out the flaw printed an in depth write-up about CVE-2024-4879 and two extra flaws (CVE-2024-5178 and CVE-2024-5217) in ServiceNow that may be chained for complete database get entry to.
Quickly, GitHub was once flooded with operating exploits in accordance with the write-up and bulk community scanners for CVE-2024-4879, which danger actors nearly instantly leveraged to search out inclined cases, stories Resecurity.
The continuing exploitation observed through Resecurity makes use of a payload injection to test for a particular outcome within the server reaction, adopted through a second-stage payload that tests the database contents.
If a hit, the attacker dumps consumer lists and account credentials. Resecurity says normally, those had been hashed, however one of the vital breached cases uncovered plaintext credentials.
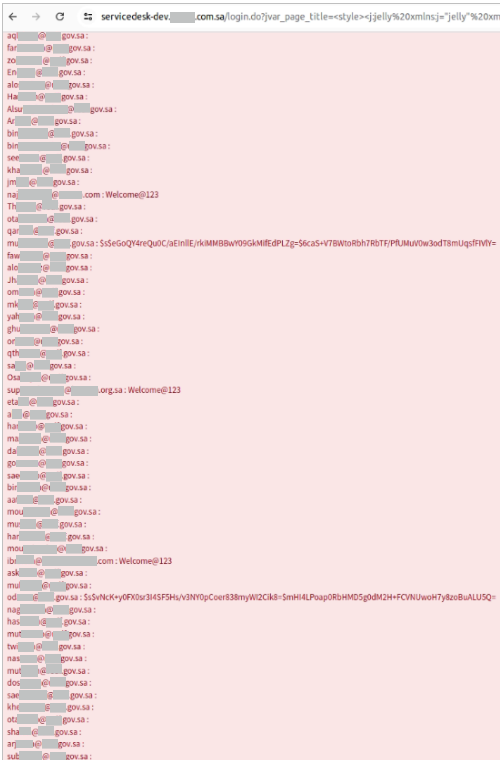
Supply: Resecurity
Resecurity has observed increased chatter in regards to the ServiceNow flaws on underground boards, particularly through customers in the hunt for get entry to to IT carrier desks and company portals, indicating a top pastime from the cybercrime neighborhood.
ServiceNow has made fixes to be had for all 3 vulnerabilities previous this month in separate announcements for CVE-2024-4879, CVE-2024-5178, and CVE-2024-5217.
Customers are really helpful to test the mounted model indicated at the advisories and ensure that they’ve implemented the patch on all cases or do it once imaginable in the event that they have not.

