A Telegram for Android zero-day vulnerability dubbed ‘EvilVideo’ allowed attackers to ship malicious Android APK payloads disguised as video information.
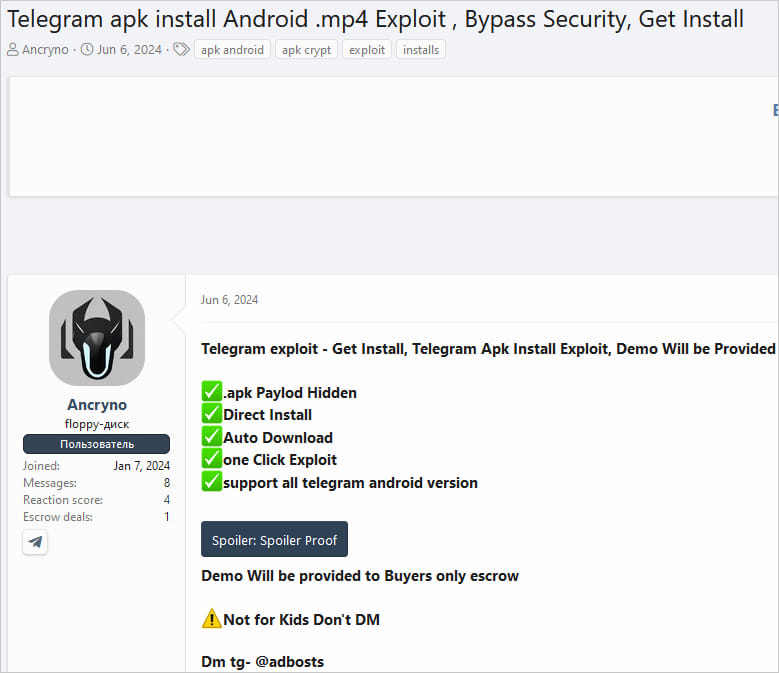
A danger actor named ‘Ancryno’ first started promoting the Telegram zero-day exploit on June 6, 2024, in a publish at the Russian-speaking XSS hacking discussion board, declaring the flaw existed in Telegram v10.14.4 and older.
ESET researchers came upon the flaw after a PoC demonstration used to be shared on a public Telegram channel, letting them download the malicious payload.
Supply: ESET
ESET showed the exploit labored in Telegram v10.14.4 and older and named it ‘EvilVideo.’ ESET researcher Lukas Stefanko responsibly disclosed the flaw to Telegram on June 26 and once more on July 4, 2024.
Telegram spoke back on July 4, declaring they had been investigating the document after which patched the vulnerability in model 10.14.5, launched on July 11, 2024.
This implies the danger actors had no less than 5 weeks to milk the zero-day prior to it used to be patched.
Whilst it’s unclear if the flaw used to be actively exploited in assaults, ESET shared a command and regulate server (C2) utilized by the payloads at ‘infinityhackscharan.ddns[.]internet.’
BleepingComputer discovered two malicious APK information the usage of that C2 on VirusTotal [1, 2] that fake to be Avast Antivirus or an ‘xHamster Top class Mod.’
Telegram zero-day exploit
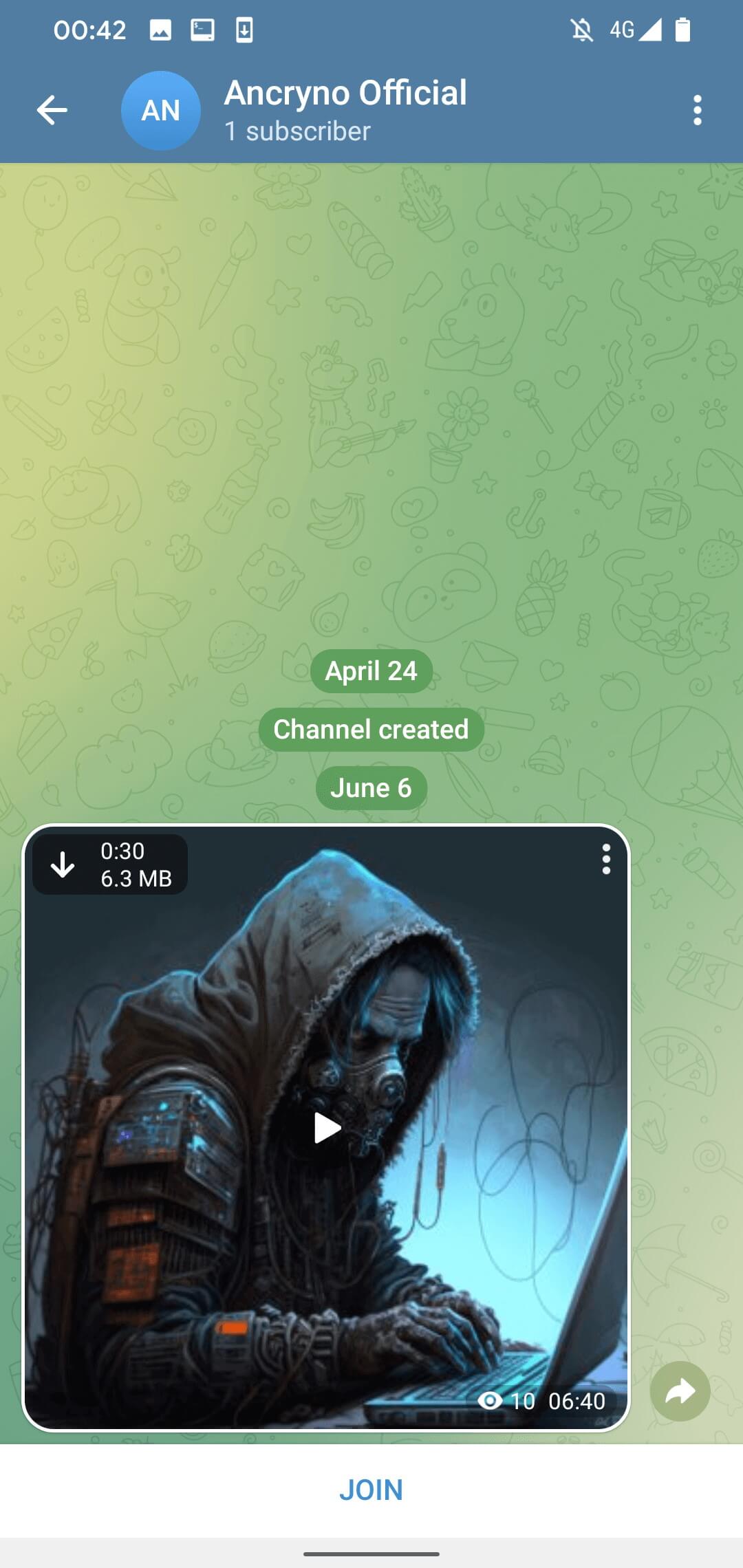
The EvilVideo zero-day flaw best labored on Telegram for Android and allowed attackers to create specifically crafted APK information that, when despatched to different customers on Telegram, seem as embedded movies.
ESET believes that the exploit makes use of the Telegram API to programmatically create a message that looks to turn a 30-second video.
Supply: ESET
On its default environment, the Telegram app on Android mechanically downloads media information, so channel individuals obtain the payload on their software when they open the dialog.
For customers who’ve disabled the auto-download, a unmarried faucet at the video preview is sufficient to begin the document obtain.
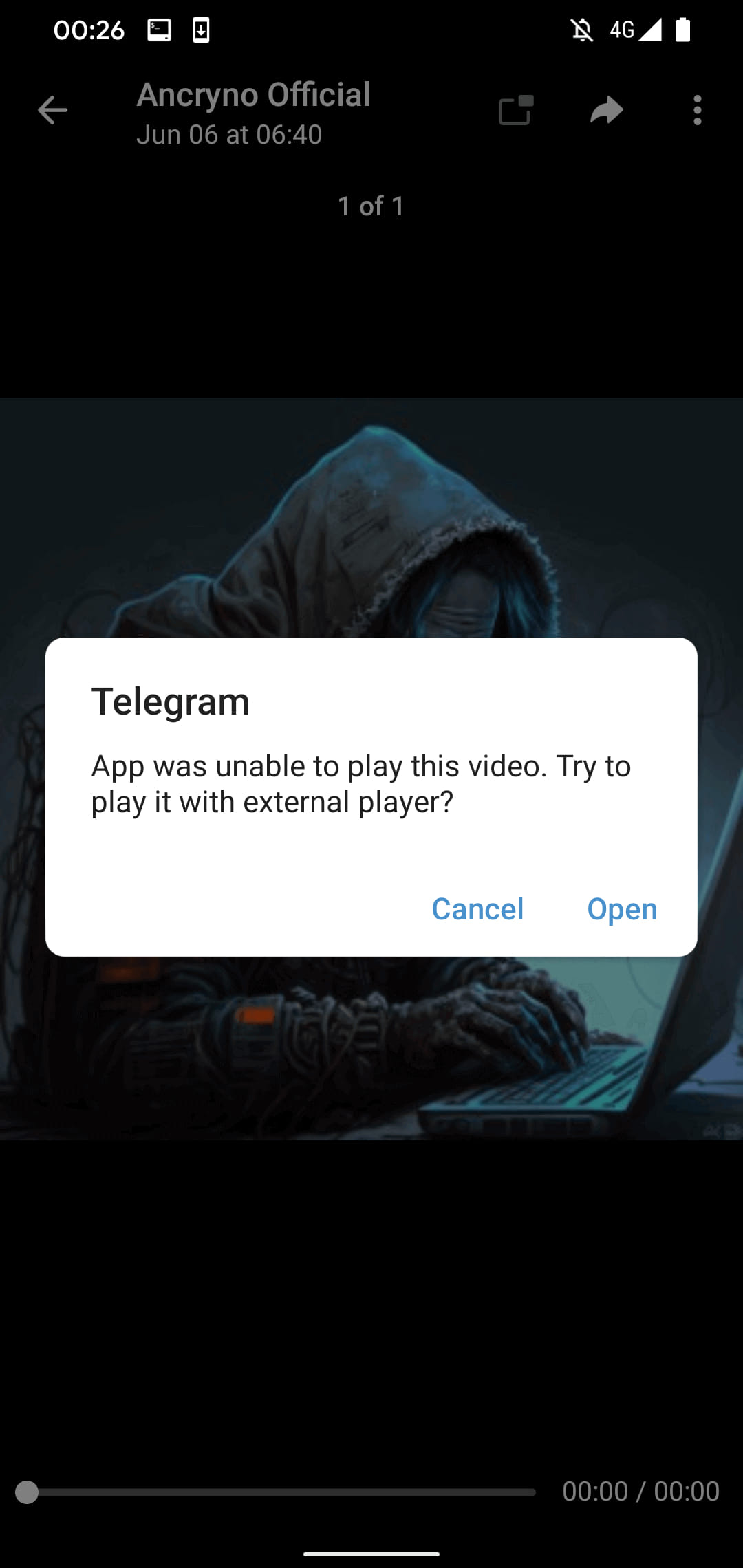
When customers try to play the pretend video, Telegram suggests the usage of an exterior participant, which would possibly reason recipients to faucet the “Open” button and execute the payload.
Supply: ESET
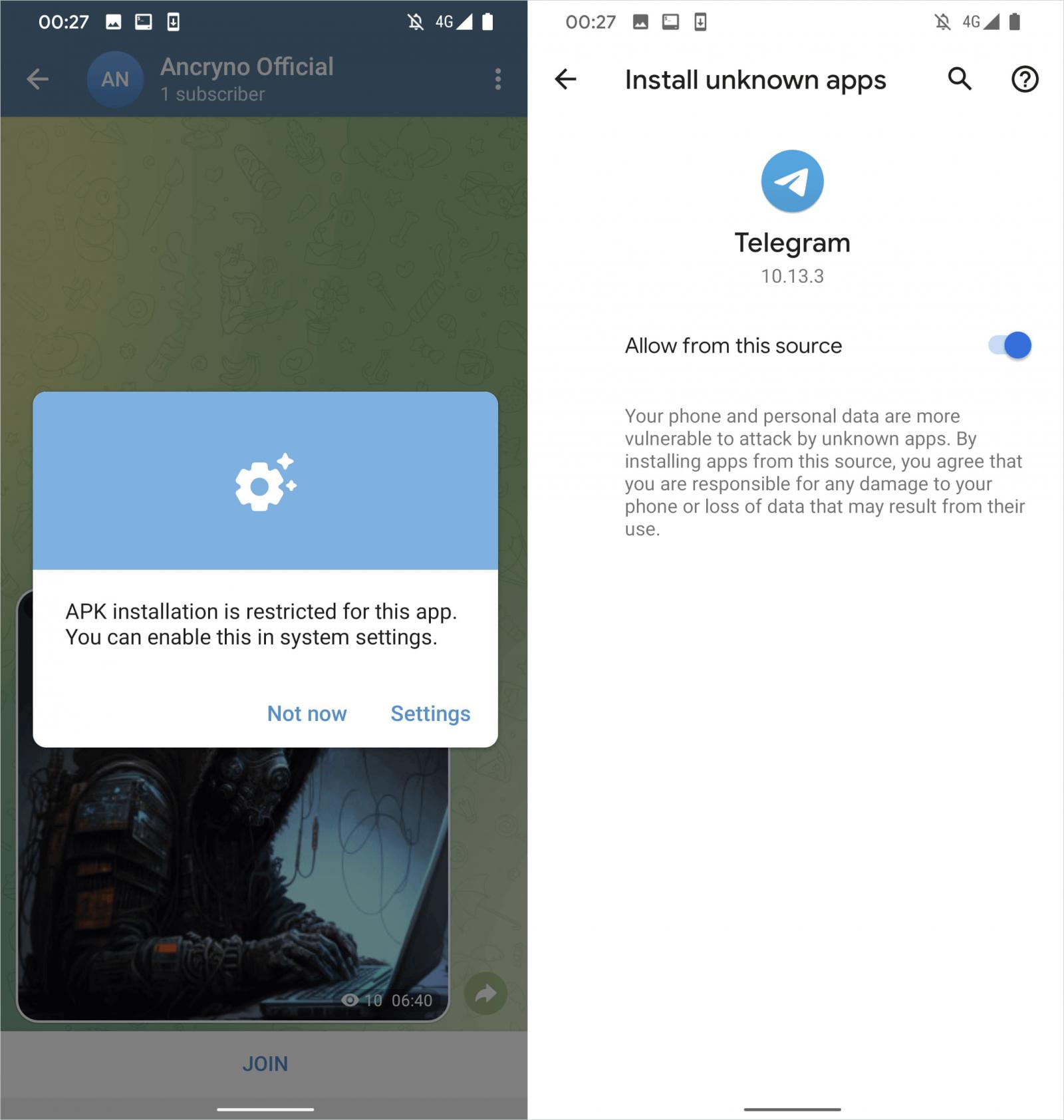
Subsequent, an extra step is needed: the sufferer should allow the set up of unknown apps from the software settings, permitting the malicious APK document to put in at the software.
Supply: ESET
Despite the fact that the danger actor claims the exploit is “one-click,” the truth that it calls for a couple of clicks, steps, and explicit settings for a malicious payload to be achieved on a sufferer’s software considerably reduces the chance of a a success assault.
ESET examined the exploit on Telegram’s internet consumer and Telegram Desktop and located that it does not paintings there since the payload is handled as an MP4 video document.
Telegram’s repair in model 10.14.5 now shows the APK document appropriately within the preview, so recipients can now not be deceived by way of what would seem as video information.
In the event you just lately gained video information that asked an exterior app to play by means of Telegram, carry out a filesystem scan the usage of a cell safety suite to find and take away the payloads out of your software.
Usually, Telegram video information are saved in ‘/garage/emulated/0/Telegram/Telegram Video/’ (inside garage) or in ‘/garage/<SD Card ID>/Telegram/Telegram Video/’ (exterior garage).
ESET shared a video demonstrating the Telegram zero-day exploit, which can also be watched underneath.

