Risk actors are already seeking to exploit a crucial authentication bypass flaw in Development MOVEit Switch, lower than an afternoon after the seller disclosed it.
MOVEit Switch is a controlled report switch (MFT) answer utilized in endeavor environments to safely switch recordsdata between trade companions and consumers the usage of the SFTP, SCP, and HTTP protocols.
The brand new safety factor won the identifier CVE-2024-5806 and lets in attackers to avoid the authentication procedure within the Protected Report Switch Protocol (SFTP) module, which is answerable for report switch operations over SSH.
An attacker leveraging this flaw may get entry to delicate knowledge saved at the MOVEit Switch server, add, obtain, delete, or regulate recordsdata, and intercept or tamper with report transfers.
Exploit code to be had
Risk tracking platform Shadowserver Basis reported seeing exploitation makes an attempt in a while after Development printed the bulletin on CVE-2024-5806, so hackers are already attacking prone endpoints.
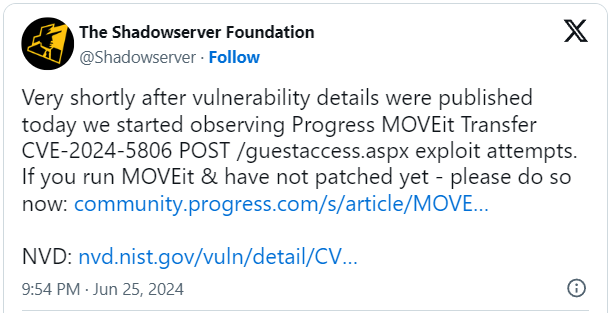
Community scans through Censys point out that there are lately round 2,700 internet-exposed MOVEit Switch circumstances, maximum situated in the United States, UK, Germany, Canada, and the Netherlands.
Supply: Censys
Then again, the proportion of those that haven’t carried out the protection updates and/or the proposed mitigations for the third-party flaw is unknown.
ShadowServer’s file of exploitation makes an attempt comes after offensive safety corporate watchTowr printed technical information about the vulnerability, how it may be exploited, and what defenders will have to search for within the logs to test for indicators of exploitation.
watchTowr additionally supplies a technical research of the way attackers can manipulate SSH public key paths to drive the server to authenticate the usage of attacker-controlled paths, probably exposing Internet-NTLMv2 hashes.
Moreover, proof-of-concept exploit code for CVE-2024-5806 is already publicly to be had from watchTowr and vulnerability researcher Sina Kheirkhah.
With this data out, the assaults will unquestionably select up tempo within the following days, so it’s a very powerful for organizations to use the similar safety updates and mitigations once conceivable.
Patches launched for CVE-2024-5806
As Development defined within the safety bulletin, CVE-2024-5806 affects the next product variations:
- 2023.0.0 prior to 2023.0.11
- 2023.1.0 prior to 2023.1.6
- 2024.0.0 prior to 2024.0.2
Fixes had been made to be had in MOVEit Switch 2023.0.11, 2023.1.6, and 2024.0.2, to be had at the Development Group portal.
Consumers with no present upkeep settlement will have to right away touch the Renewals group or Development spouse consultant to unravel the problem.
MOVEit Cloud consumers don’t wish to take any motion to mitigate the crucial flaw, as patches have already been robotically deployed.
Along with the flaw itself, Development notes that it came upon a separate vulnerability on a third-party part utilized in MOVEit Switch, which elevates the hazards related to CVE-2024-5806.
To mitigate this flaw till a repair from the third-party dealer is made to be had, device directors are prompt to dam Far flung Desktop Protocol (RDP) get entry to to the MOVEit Switch servers and prohibit outbound connections to recognized/depended on endpoints.
Development additionally launched a safety bulletin a couple of identical authentication bypass factor, CVE-2024-5805, which affects MOVEit Gateway 2024.0.0.
MOVEit is extensively used within the endeavor surroundings and hackers are holding a eye on vulnerabilities and exploits to be had at the product, particularly since Clop ransomware leveraged a 0 day remaining yr to breach and therefore extort hundreds of organizations.
