Danger actors are actively exploiting a SolarWinds Serv-U path-traversal vulnerability, leveraging publicly to be had proof-of-concept (PoC) exploits.
Even supposing the assaults don’t seem specifically subtle, the noticed process underscores the danger posed via unpatched endpoints, emphasizing the pressing want for directors to use the safety updates.
The CVE-2024-28995 flaw
The vulnerability, CVE-2024-28995, is a high-severity listing traversal flaw, permitting unauthenticated attackers to learn arbitrary recordsdata from the filesystem via crafting particular HTTP GET requests.
The vulnerability arises from inadequate validation of direction traversal sequences, enabling attackers to avoid safety exams and get right of entry to delicate recordsdata.
The flaw affects the next SolarWinds merchandise:
- Serv-U FTP Server 15.4
- Serv-U Gateway 15.4
- Serv-U MFT Server 15.4
- Serv-U Record Server 15.4.2.126 and previous
Older variations (15.3.2 and previous) also are affected however will succeed in the tip of lifestyles in February 2025 and are already unsupported.
Exploiting the flaw might disclose delicate information from unauthorized report get right of entry to, doubtlessly resulting in prolonged compromise.
SolarWinds launched the 15.4.2 Hotfix 2, model 15.4.2.157, on June 5, 2024, to handle this vulnerability via introducing progressed validation mechanisms.
Public exploits to be had
Over the weekend, Rapid7 analysts revealed a technical write-up that supplied detailed steps to milk the listing traversal vulnerability in SolarWinds Serv-U to learn arbitrary recordsdata from the affected gadget.
An afternoon later, an impartial Indian researcher launched a PoC exploit and a bulk scanner for CVE-2024-28995 on GitHub.
On Monday, Rapid7 warned about how trivial the flaw is to milk, estimating the collection of internet-exposed and doubtlessly inclined cases between 5,500 and 9,500.
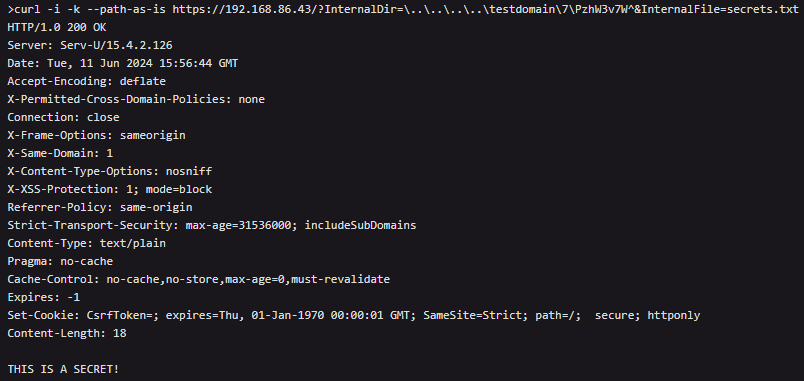
Supply: Rapid7
GreyNoise arrange a honeypot that mimics a inclined Serv-U gadget to observe and analyze exploitation makes an attempt for CVE-2024-28995.
The analysts noticed more than a few assault methods, together with hands-on keyboard movements indicating handbook makes an attempt to milk the vulnerability, in addition to automatic makes an attempt.
Attackers use platform-specific direction traversal sequences, bypassing safety exams the use of unsuitable slashes, which the Serv-U gadget later corrects, permitting unauthorized report get right of entry to.
Conventional payloads on Home windows are ‘GET /?InternalDir=/../../../../home windows&InternalFile=win.ini’ and on Linux it’s ‘GET /?InternalDir=……..and so on&InternalFile=passwd.’
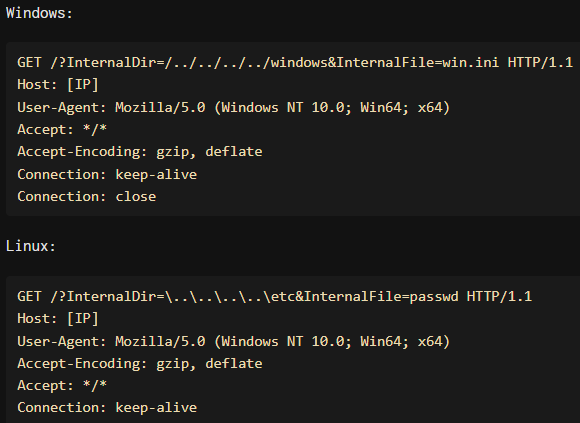
Supply: GreyNoise
Essentially the most incessantly centered recordsdata observed via Greynoise are:
- and so on/passwd (comprises person account information on Linux)
- /ProgramData/RhinoSoft/Serv-U/Serv-U-StartupLog.txt (comprises startup logs data for the Serv-U FTP server)
- /home windows/win.ini (initialization report containing Home windows configuration settings)
Attackers goal the ones recordsdata to escalate their privileges or discover secondary alternatives within the breached community.
GreyNoise experiences circumstances the place the attackers seem to copy-paste exploits with out checking out, leading to failed makes an attempt.
In different exploitation makes an attempt from China, the attackers show off patience, adaptability, and higher working out.
GreyNoise says they experimented with other payloads and codecs for 4 hours and altered their means in keeping with server responses.
With showed assaults underway, gadget directors should observe the to be had fixes once conceivable.
