Researchers discovered part a dozen vulnerabilities of various severity impacting Netgear WNR614 N300, a budget-friendly router that proved fashionable amongst house customers and small companies.
The software reached end-of-life (EoL) and is not supported by means of Netgear however it is nonetheless provide in lots of environments because of its reliability, ease of use, and function.
Researchers at RedFox Safety found out within the router six vulnerabilities that vary from authentication bypass and susceptible password coverage to storing passwords in undeniable textual content and Wi-Fi Secure Setup (WPS) PIN publicity:
CVE-2024-36787: lets in an attacker to circumvent authentication and get right of entry to the executive interface by the use of unspecified vectors. The flaw allows unauthorized get right of entry to to the router’s settings, posing a serious danger to community safety and delicate person information.
Supply: RedFox
CVE-2024-36788: the router has unsuitable environment of the HTTPOnly flag for cookies. An attacker may just leverage the vulnerability to intercept and get right of entry to delicate communications between the router and the gadgets connecting to it.
CVE-2024-36789: lets in attackers to create passwords that don’t conform to correct safety requirements or even settle for a unmarried persona as a password for the administrator account. This may just result in unauthorized get right of entry to, community manipulation, and possible information publicity.
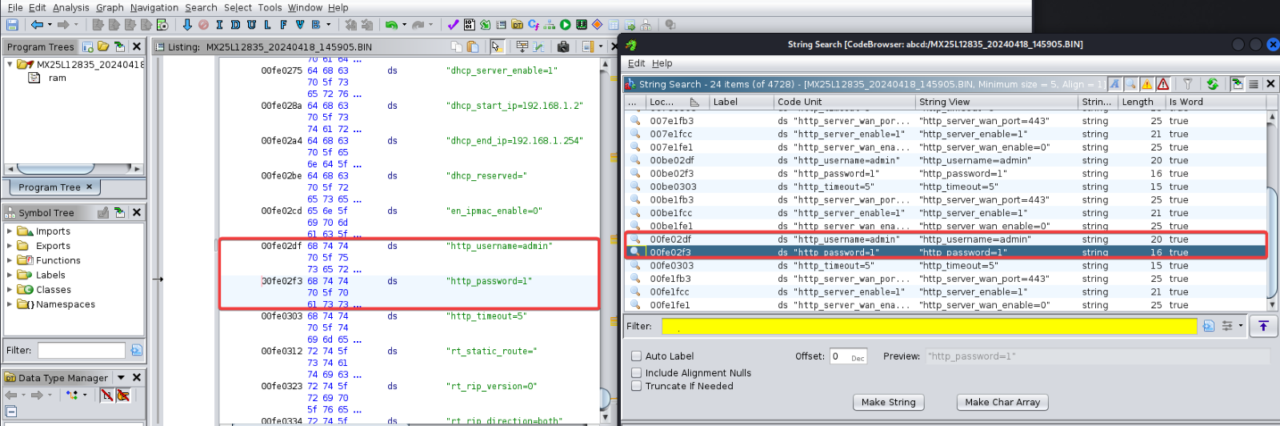
CVE-2024-36790: the router retail outlets credentials in undeniable textual content, which makes it simple for an attacker to acquire unauthorized get right of entry to, manipulate the router, and disclose delicate information.
Supply: RedFox
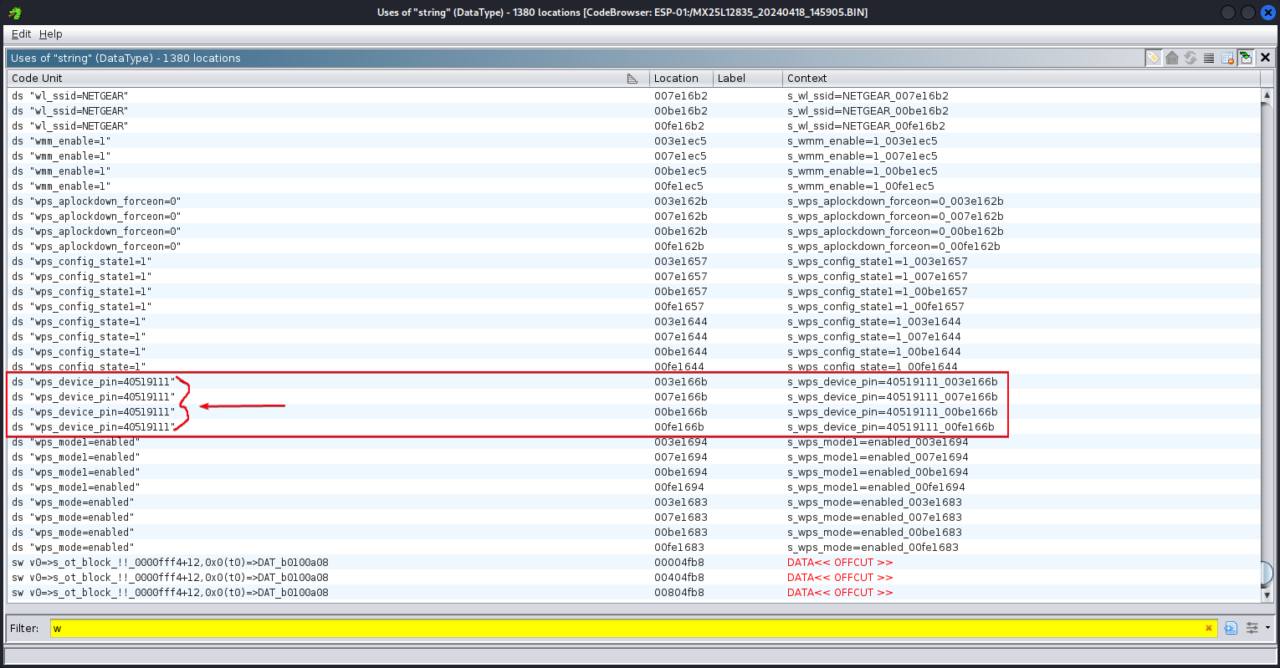
CVE-2024-36792: the implementation of the WPS Wi-Fi characteristic lets in attackers to realize get right of entry to to the router’s PIN. This exposes the router to possible unauthorized get right of entry to and manipulation.
Supply: RedFox
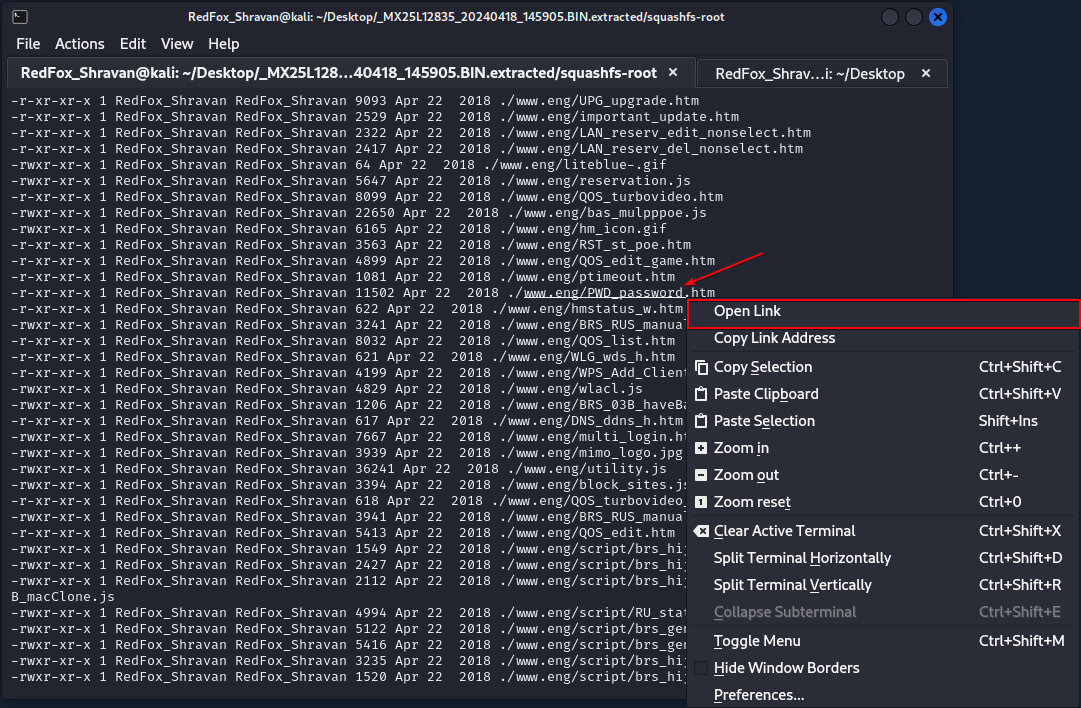
CVE-2024-36795: insecure permissions that permit attackers to get right of entry to URLs and directories embedded throughout the router’s firmware. This heightens the chance of unauthorized community get right of entry to and keep an eye on.
Because the router has reached EoL, Netgear isn’t anticipated to free up safety updates for the vulnerabilities. If changing the software isn’t an choice nowadays, customers are strongly urged to use mitigatations that would assist save you assaults:
- Flip off faraway control options to cut back the chance of unauthorized get right of entry to.
- Use complicated, lengthy passwords and alter them ceaselessly.
- Separate the router from important methods throughout the community to restrict the affect of any possible breach.
- Make sure that the router makes use of HTTPS and use browser settings that implement HTTPS to protected all communications and offer protection to towards interception.
- Flip off WPS to stop attackers from exploiting this selection and gaining unauthorized get right of entry to.
- Transfer to WPA3 for enhanced safety over older protocols.
- Limit get right of entry to to the router’s administrative interface.
Then again, customers that also depend on Netgear WNR614 must believe changing it with a fashion this is actively supported by means of its producer and offers higher safety.
