The Russian GRU-backed risk actor APT28 has been attributed as in the back of a chain of campaigns focused on networks throughout Europe with the HeadLace malware and credential-harvesting internet pages.
APT28, additionally recognized via the names BlueDelta, Fancy Endure, Wooded area Snowfall, FROZENLAKE, Iron Twilight, ITG05, Pawn Hurricane, Sednit, Sofacy, and TA422, is a sophisticated chronic risk (APT) staff affiliated with Russia’s strategic army intelligence unit, the GRU.
The hacking workforce operates with a top degree of stealth and class, steadily demonstrating their adaptability thru deep preparedness and customized tooling, and depending on respectable web products and services (LIS) and residing off-the-land binaries (LOLBins) to hide their operations inside common community visitors.
“From April to December 2023, BlueDelta deployed Headlace malware in 3 distinct stages the use of geofencing tactics to focus on networks all through Europe with a heavy center of attention on Ukraine,” Recorded Long run’s Insikt Crew mentioned.
“BlueDelta’s espionage actions replicate a broader technique aimed toward accumulating intelligence on entities with army importance to Russia within the context of its ongoing aggression towards Ukraine.”

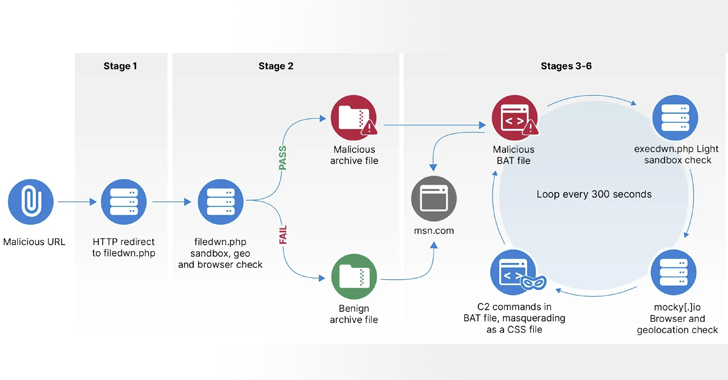
HeadLace, as in the past documented via the Laptop Emergency Reaction Crew of Ukraine (CERT-UA), Zscaler, Proofpoint, and IBM X-Drive, is sent by way of spear-phishing emails containing malicious hyperlinks that, when clicked, start up a multi-stage an infection collection to drop the malware.
BlueDelta is alleged to have hired a seven-stage infrastructure chain right through the primary section to ship a malicious Home windows BAT script (i.e., HeadLace) that is in a position to downloading and working follow-on shell instructions, matter to sandbox and geofencing exams.
The second one section, which commenced on September 28, 2023, is notable for the use of GitHub as the place to begin of the redirection infrastructure, whilst the 3rd section switched to the use of PHP scripts hosted on InfinityFree starting October 17, 2023.
“The final detected task in section 3 used to be in December2023,” the corporate mentioned. “Since then, BlueDelta most probably ceased the use of InfinityFree website hosting and appreciated website hosting infrastructure on webhook[.]website online and mocky[.]io at once.”
BlueDelta has additionally been discovered to adopt credential harvesting operations designed to focus on products and services like Yahoo! and UKR[.]web via serving lookalike pages and in the long run trick sufferers into getting into their credentials.
Every other methodology concerned growing devoted internet pages on Mocky that engage with a Python script working on compromised Ubiquiti routers to exfiltrate the entered credentials. Previous this February, a U.S.-led legislation enforcement operation disrupted a botnet comprising Ubiquiti EdgeRouters that used to be put to make use of via APT28 for this goal.
Objectives of the credential harvesting task integrated the Ukrainian Ministry of Defence, Ukrainian guns import and export firms, Ecu railway infrastructure, and a suppose tank based totally in Azerbaijan.

“Effectively infiltrating networks related to Ukraine’s Ministry of Defence and Ecu railway programs may just permit BlueDelta to assemble intelligence that probably shapes battlefield techniques and broader army methods,” Recorded Long run mentioned.
“Additionally, BlueDelta’s passion within the Azerbaijan Heart for Financial and Social Construction suggests an time table to know and most likely affect regional insurance policies.”
The improvement comes as some other state-sponsored Russian risk staff known as Turla has been noticed leveraging human rights seminar invites as phishing e mail decoys to execute a payload very similar to the TinyTurla backdoor the use of the Microsoft Construct Engine (MSBuild).
