A up to now undocumented cyber espionage-focused risk actor named LilacSquid has been related to centered assaults spanning more than a few sectors in the USA (U.S.), Europe, and Asia as a part of an information robbery marketing campaign since a minimum of 2021.
“The marketing campaign is aimed at setting up long-term get entry to to compromised sufferer organizations to permit LilacSquid to siphon knowledge of pastime to attacker-controlled servers,” Cisco Talos researcher Asheer Malhotra stated in a brand new technical record printed as of late.
Objectives come with knowledge era organizations construction device for the analysis and commercial sectors within the U.S, power corporations in Europe, and the pharmaceutical sector in Asia, indicating a wide victimology footprint.
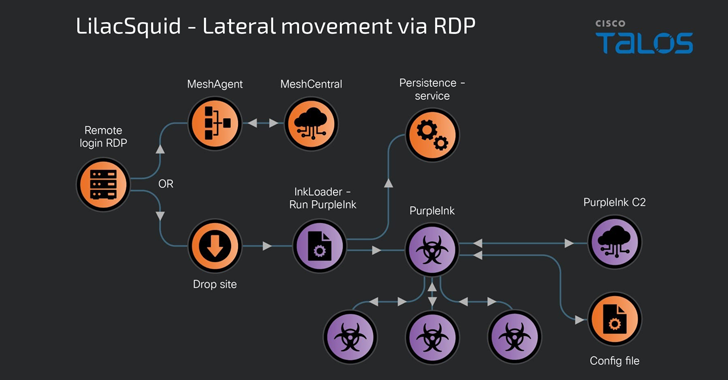
Assault chains are recognized to take advantage of both publicly recognized vulnerabilities to breach internet-facing software servers or employ compromised far off desktop protocol (RDP) credentials to ship a mixture of open-source equipment and customized malware.

The marketing campaign’s maximum unique characteristic is using an open-source far off control software referred to as MeshAgent, which serves as a conduit to ship a bespoke model of Quasar RAT codenamed PurpleInk.
Trade an infection procedures leveraging compromised RDP credentials showcase a fairly other modus operandi, through which the risk actors select to both deploy MeshAgent or drop a .NET-based loader dubbed InkLoader to drop PurpleInk.

“A a hit login by means of RDP results in the obtain of InkLoader and PurpleInk, copying those artifacts into desired directories on disk and the next registration of InkLoader as a provider this is then began to deploy InkLoader and, in flip, PurpleInk,” Malhotra stated.
PurpleInk, actively maintained by means of LilacSquid since 2021, is each closely obfuscated and flexible, permitting it to run new programs, carry out record operations, get device knowledge, enumerate directories and processes, release a far off shell, and connect with a selected far off cope with equipped by means of a command-and-control (C2) server.
Talos stated it known any other customized software referred to as InkBox that is stated to were utilized by the adversary to deploy PurpleInk previous to InkLoader.

The incorporation of MeshAgent as a part of their post-compromise playbooks is noteworthy partially because of the truth that it is a tactic up to now followed by means of a North Korean risk actor named Andariel, a sub-cluster throughout the notorious Lazarus Team, in assaults concentrated on South Korean corporations.
Some other overlap issues using tunneling equipment to take care of secondary get entry to, with LilacSquid deploying Protected Socket Funneling (SSF) to create a verbal exchange channel to its infrastructure.
“More than one techniques, tactics, equipment, and procedures (TTPs) applied on this marketing campaign undergo some overlap with North Korean APT teams, reminiscent of Andariel and its father or mother umbrella team, Lazarus,” Malhotra stated.
