The U.S. Cybersecurity & Infrastructure Safety Company (CISA) has added two vulnerabilities in its Identified Exploited Vulnerabilities (KEV) catalog, together with a Linux kernel privilege elevation flaw.
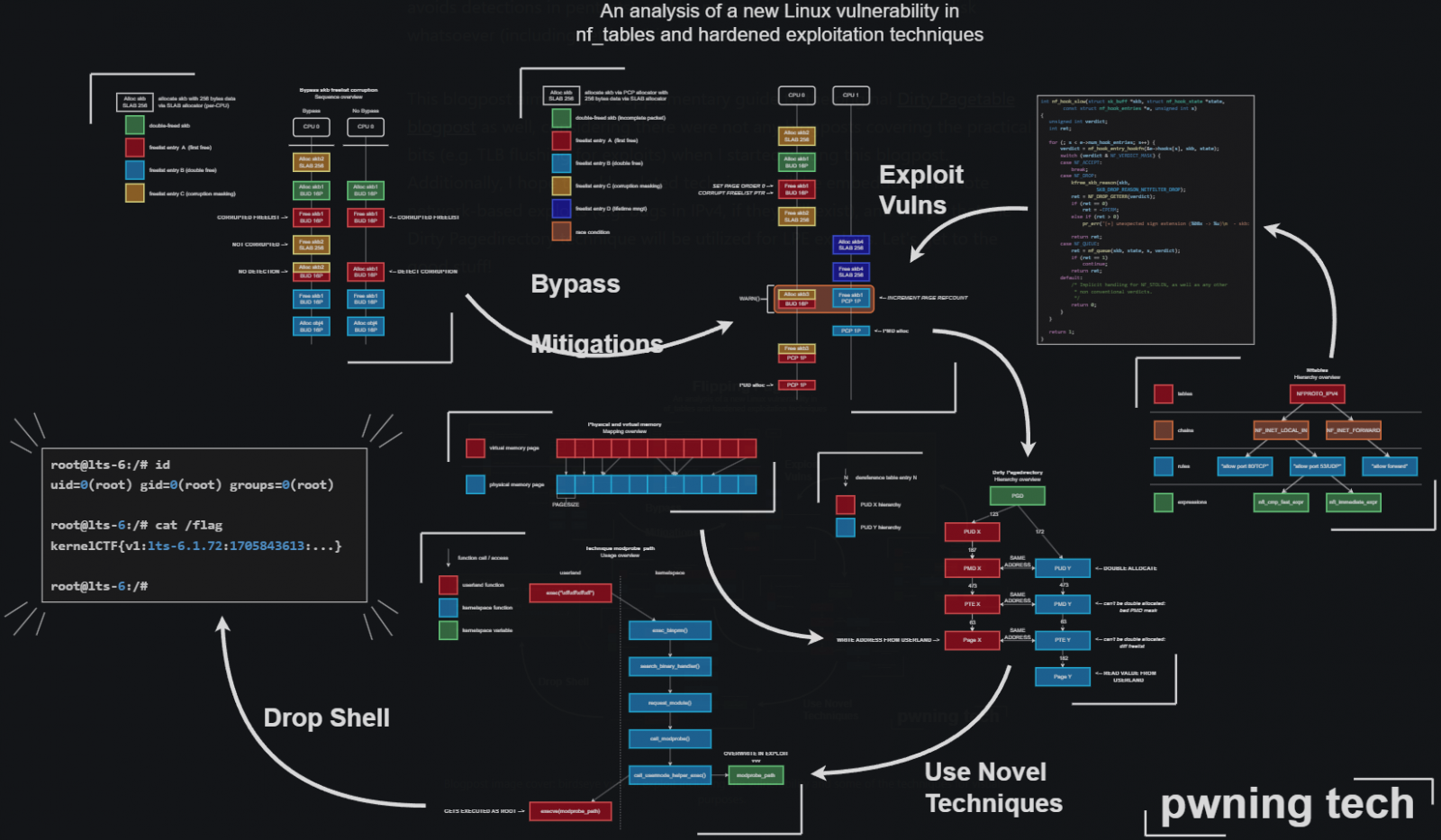
The high-severity flaw tracked as CVE-2024-1086 was once first disclosed on January 31, 2024, as a use-after-free drawback within the netfilter: nf_tables part, however was once first offered by way of a devote in February 2014.
Netfilter is a framework supplied by way of the Linux kernel that permits quite a lot of networking-related operations, corresponding to packet filtering, community cope with translation (NAT), and packet mangling.
The vulnerability is led to for the reason that ‘nft_verdict_init()’ serve as permits sure values for use as a drop error throughout the hook verdict, inflicting the ‘nf_hook_slow()’ serve as to execute a double loose when NF_DROP is issued with a drop error that resembles NF_ACCEPT.
Exploitation of CVE-2024-1086 permits an attacker with native get entry to to succeed in privilege escalation at the goal device, doubtlessly gaining root-level get entry to.
The problem was once fastened by way of a devote submitted in January 2024, which rejects QUEUE/DROP verdict parameters, thus combating exploitation.
The repair has been backported to more than one solid kernel variations as indexed under:
- v5.4.269 and later
- v5.10.210 and later
- v6.6.15 and later
- v4.19.307 and later
- v6.1.76 and later
- v5.15.149 and later
- v6.7.3 and later
In past due March 2024, a safety researcher the usage of the alias ‘Notselwyn’ printed an in depth write-up and proof-of-concept (PoC) exploit on GitHub, showcasing how to succeed in native privilege escalation by way of exploiting the flaw on Linux kernel variations between 5.14 and six.6.
Whilst maximum Linux distrobutions driven out fixes relatively temporarily, Crimson Hat had now not driven out a repair till March, making it imaginable that risk actors used the general public exploit on compromised programs.
CISA didn’t proportion particular information about how the vulnerability is exploited, however BleepingComputer has observed posts on hacking boards concerning the public exploits.
The cybersecurity company has now given federal businesses till June 20, 2024, to use the to be had patches.
If updating isn’t imaginable, admins are beneficial to use the next mitigations:
- Blocklist ‘nf_tables’ if it isn’t wanted/actively used.
- Limit get entry to to person namespaces to restrict the assault floor.
- Load the Linux Kernel Runtime Guard (LKRG) module (may cause instability)
The second one flaw CISA added at the KEV catalog this time, additionally environment the due date to June 20, is CVE-2024-24919, a knowledge disclosure vulnerability impacting VPN gadgets from Test Level.
Following the seller’s disclosure and safety replace free up for this flaw, researchers from Watchtowr Labs printed their research, underlining that the vulnerability is some distance worse than what Test Level’s bulletin mirrored.
