Brazilian banking establishments are the objective of a brand new marketing campaign that distributes a customized variant of the Home windows-based AllaKore faraway get right of entry to trojan (RAT) known as AllaSenha.
The malware is “particularly aimed toward stealing credentials which might be required to get right of entry to Brazilian financial institution accounts, [and] leverages Azure cloud as command-and-control (C2) infrastructure,” French cybersecurity corporate HarfangLab stated in a technical research.
Goals of the marketing campaign come with banks similar to Banco do Brasil, Bradesco, Banco Safra, Caixa Econômica Federal, Itaú Unibanco, Sicoob, and Sicredi. The preliminary get right of entry to vector, even though no longer definitively showed, issues against using malicious hyperlinks in phishing messages.
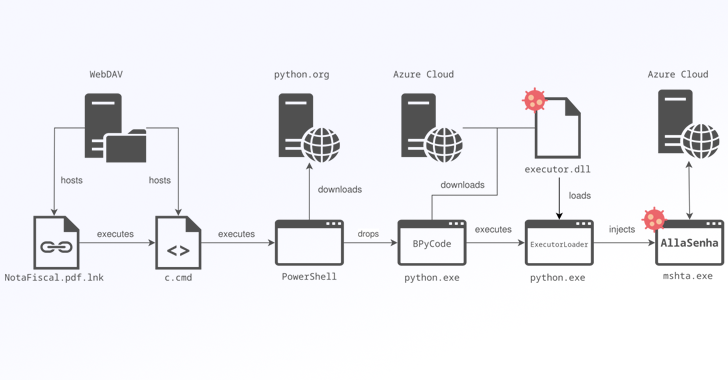
The place to begin of the assault is a malicious Home windows shortcut (LNK) record that masquerades as a PDF report (“NotaFiscal.pdf.lnk”) hosted on a WebDAV server since no less than March 2024. There could also be proof to signify that the danger actors in the back of the job in the past abused legit products and services like Autodesk A360 Pressure and GitHub to host the payloads.
The LNK record, when introduced, executes a Home windows command shell that is designed to open a decoy PDF record to the recipient, whilst concurrently retrieving a BAT payload named “c.cmd” from the similar WebDAV server location.
Dubbed the BPyCode launcher, the record launches a Base64-encoded PowerShell command, which due to this fact downloads the Python binary from the reputable www.python[.]org site so as to execute a Python script codenamed BPyCode.

BPyCode, for its section, purposes as a downloader for a dynamic-link library (“executor.dll”) and operating it in reminiscence. The DLL is fetched from probably the most domains generated by the use of a site era set of rules (DGA).
“Generated hostnames appear to compare the ones which might be related to the Microsoft Azure Purposes provider, a serverless infrastructure that on this case would permit operators to simply deploy and rotate their staging infrastructure,” the corporate stated.
In particular, BPyCode retrieves a pickle record that incorporates 3 recordsdata: A 2d Python loader script, a ZIP archive containing the PythonMemoryModule bundle, and some other ZIP archive containing “executor.dll.”
The brand new Python loader script is then introduced to load executor.dll, a Borland Delphi-based malware often known as ExecutorLoader, in reminiscence the usage of PythonMemoryModule. ExecutorLoader is essentially tasked with deciphering and executing AllaSenha by way of injecting it into a valid mshta.exe procedure.
Along with stealing on-line banking account credentials from internet browsers, AllaSenha comes having the ability to show overlay home windows so as to seize two-factor authentication (2FA) codes or even trick a sufferer into scanning a QR code to approve a fraudulent transaction initiated by way of the attackers.
“All AllaSenha samples […] use Access_PC_Client_dll.dll as their unique record identify,” HarfangLab famous. “This identify can particularly be discovered within the KL Gorki challenge, a banking malware which turns out to mix elements of each AllaKore and ServerSocket.”
Additional research of the supply code related to the preliminary LNK record and AllaSenha samples has published {that a} Portuguese-speaking consumer named bert1m is most likely connected to the improvement of the malware, despite the fact that there’s no proof at this degree to signify that they’re working the equipment as smartly.
“The danger actors that perform in Latin The united states seem to be a in particular productive supply of cybercrime campaigns,” HarfangLab stated.
“Whilst nearly solely focused on Latin American folks to scouse borrow banking main points, those actors steadily finally end up compromising computer systems which might be certainly operated by way of subsidiaries or workers in Brazil, however that belong to corporations all over the international.”
The improvement comes as Forcepoint detailed malspam campaigns distributing some other Latin The united states-focused banking trojan known as Casbaneiro (aka Metamorfo and Ponteiro) by the use of HTML attachments with an intention to siphon sufferers’ monetary knowledge.
“The malware dispensed by the use of e-mail urges the consumer to click on at the attachment,” safety researcher Prashant Kumar stated. “The attachment accommodates malicious code which does a chain of actions and results in knowledge compromise.”
Anatsa Android Banking Trojan Sneaks into Google Play Retailer
It is not simply Home windows that has been on the receiving finish of banking trojan assaults, for Zscaler ThreatLabz disclosed main points of an Android banking malware marketing campaign that made use of decoy programs uploaded to the Google Play retailer to ship Anatsa (aka TeaBot and Infant).

Those blank dropper programs cross off as apparently risk free productiveness and software apps like PDF readers, QR code readers, and translators, and make use of an an identical an infection chain published by way of ThreatFabric previous this February to retrieve and deploy the malware from a faraway server underneath the guise of an app replace to evade detection.
The apps, that have since been taken down by way of Google, are indexed underneath –
- com.appandutilitytools.fileqrutility (QR Reader & Document Supervisor)
- com.ultimatefilesviewer.filemanagerwithpdfsupport (PDF Reader & Document Supervisor)
In keeping with statistics to be had on Sensor Tower, PDF Reader & Document Supervisor has been put in anyplace between 500 to at least one,000 instances, whilst the QR code reader app has had installations within the vary of fifty,000 to 100,000.

“As soon as put in, Anatsa exfiltrates delicate banking credentials and fiscal knowledge from international monetary programs,” researchers Himanshu Sharma and Gajanan Khond stated. “It achieves this via using overlay and accessibility tactics, permitting it to intercept and accumulate knowledge discreetly.”
Zscaler stated it recognized over 90 malicious apps at the Play Retailer during the last few months that experience jointly had greater than 5.5 million installations and had been used to propagate quite a lot of malware households like Joker, Facestealer, Anatsa, Coper, and different spy ware.
