Taiwanese corporate QNAP has rolled out fixes for a collection of medium-severity flaws impacting QTS and QuTS hero, a few of which may well be exploited to reach code execution on its network-attached garage (NAS) home equipment.
The problems, which affect QTS 5.1.x and QuTS hero h5.1.x, are indexed beneath –
- CVE-2024-21902 – An fallacious permission project for serious useful resource vulnerability that would permit authenticated customers to learn or alter the useful resource by the use of a community
- CVE-2024-27127 – A double unfastened vulnerability that would permit authenticated customers to execute arbitrary code by the use of a community
- CVE-2024-27128, CVE-2024-27129, and CVE-2024-27130 – A suite of buffer overflow vulnerabilities that would permit authenticated customers to execute arbitrary code by the use of a community
The entire shortcomings, that require a legitimate account on NAS gadgets, were addressed in QTS 5.1.7.2770 construct 20240520 and QuTS hero h5.1.7.2770 construct 20240520. Aliz Hammond of watchTowr Labs has been credited with finding and reporting the failings on January 3, 2024.

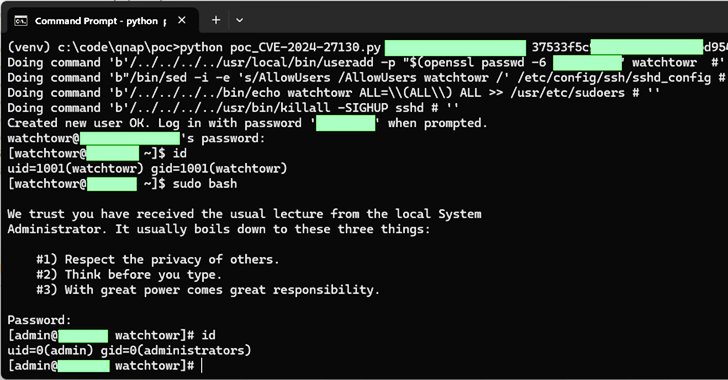
“The CVE-2024-27130 vulnerability, which has been reported below WatchTowr ID WT-2023-0054, is brought about through the unsafe use of the ‘strcpy’ serve as within the No_Support_ACL serve as, which is used by the get_file_size request within the proportion.cgi script,” QNAP mentioned.
“This script is used when sharing media with exterior customers. To take advantage of this vulnerability, an attacker calls for a legitimate ‘ssid’ parameter, which is generated when a NAS person stocks a report from their QNAP tool.”
It additionally identified that every one QTS 4.x and 5.x variations have Cope with House Format Randomization (ASLR) enabled, making it tough for an attacker to milk the vulnerability.
The patches arrived 4 days after the Singapore-based cybersecurity corporate launched information about a complete of 15 vulnerabilities, together with 4 separate insects which may be weaponized to circumvent authentication and execute arbitrary code.

The vulnerabilities – tracked from CVE-2023-50361 thru CVE-2023-50364 – had been resolved through QNAP on April 25, 2024, following disclosure in December 2023.
It is value noting that the corporate has but to free up fixes for CVE-2024-27131, which has been described through watchTowr as a case of “Log spoofing by the use of x-forwarded-for [that] permits customers to reason downloads to be recorded as asked from arbitrary supply location.”
QNAP mentioned CVE-2024-27131 isn’t a real vulnerability however somewhat a design selection that calls for a metamorphosis within the UI specs inside the QuLog Heart. That is anticipated to be remediated in QTS 5.2.0.
Information about 4 different vulnerabilities reported through watchTowr are these days withheld, with 3 of them these days below evaluation. The fourth factor has been assigned a CVE ID and might be fastened within the upcoming free up.

watchTowr mentioned it was once pressured to head public with the failings ultimate week after QNAP failed to handle them inside the stipulated 90-day public disclosure duration and that it was once beneficiant through giving the corporate “more than one extensions” to plug them.
In reaction, QNAP mentioned it regretted the coordination problems, pointing out it is committing to liberating fixes for high- or critical-severity flaws inside of 45 days. Fixes for medium-severity vulnerabilities might be launched inside of 90 days.
“We say sorry for any inconvenience this will likely have brought about and are dedicated to bettering our security features regularly,” it added. “Our objective is to paintings carefully with researchers international to verify the best quality of safety for our merchandise.”
With vulnerabilities in QNAP NAS gadgets exploited previously through ransomware attackers, customers are really helpful to the newest variations of QTS and QuTS hero once imaginable to mitigate possible threats.
