Cybersecurity researchers have found out a brand new cryptojacking marketing campaign that employs weak drivers to disable identified safety answers (EDRs) and thwart detection in what is referred to as a Convey Your Personal Prone Motive force (BYOVD) assault.
Elastic Safety Labs is monitoring the marketing campaign beneath the title REF4578 and the principle payload as GHOSTENGINE. Earlier analysis from Chinese language cybersecurity company Antiy Labs has codenamed the job as HIDDEN SHOVEL.
“GHOSTENGINE leverages weak drivers to terminate and delete identified EDR brokers that may most probably intervene with the deployed and well known coin miner,” Elastic researchers Salim Bitam, Samir Bousseaden, Terrance DeJesus, and Andrew Pease mentioned.
“This marketing campaign concerned an unusual quantity of complexity to verify each the set up and endurance of the XMRig miner.”
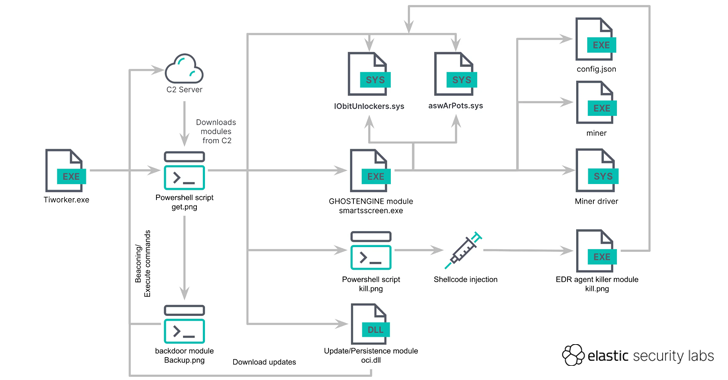
All of it begins with an executable record (“Tiworker.exe”), which is used to run a PowerShell script that retrieves an obfuscated PowerShell script that masquerades as a PNG symbol (“get.png”) to fetch further payloads from a command-and-control (C2) server.
Those modules — aswArPot.sys, IObitUnlockers.sys, curl.exe, smartsscreen.exe, oci.dll, backup.png, and kill.png — are introduced at the inflamed host after downloading them over HTTP from both the configured C2 server or a backup server in case the domain names are unavailable. It additionally comprises an FTP-based fallback mechanism.
Moreover, the malware makes an attempt to disable Microsoft Defender Antivirus, transparent a number of Home windows tournament log channels, and be sure that the C: quantity has a minimum of 10 MB of loose area to obtain recordsdata, which might be then stashed within the C:WindowsFonts folder.
“If now not, it’s going to attempt to delete vast recordsdata from the device sooner than in search of every other appropriate quantity with enough area and making a folder beneath $RECYCLE.BINFonts,” the researchers mentioned.
The PowerShell script may be designed to create 3 scheduled duties at the device to run a malicious DLL each 20 mins, release itself by the use of a batch script each hour, and execute smartsscreen.exe each 40 mins.

The core payload of the assault chain is smartsscreen.exe (aka GHOSTENGINE), whose primary goal is to deactivate safety processes the usage of the weak Avast driving force (“aswArPot.sys”), whole preliminary an infection, and execute the miner.
The protection agent binary is then deleted by the use of every other weak driving force from IObit (“iobitunlockers.sys”), following which the XMRig consumer mining program is downloaded from the C2 server and done.
The DLL record is used to verify the endurance of the malware and obtain updates from the C2 servers by way of fetching the get.png script and executing it, whilst the “backup.png” Powershell script purposes as a backdoor to allow far flung command execution at the device.
In what has been interpreted as a redundancy measure, the PowerShell script “kill.png” has identical functions as smartsscreen.exe to delete safety agent binaries by way of injecting and loading an executable record into reminiscence.
The improvement comes because the Uptycs Danger Analysis Staff found out a large-scale, ongoing operation since January 2024 that exploits identified flaws within the Log4j logging software (e.g., CVE-2021-44228) to ship an XMRig miner onto the centered hosts.

“Next to compromising a sufferer gadget, it initiated touch with a URL to fetch a shell script for the deployment of the XMRig miner, or however, in choose circumstances, it disseminated Mirai or Gafgyt malware,” safety researcher Shilpesh Trivedi mentioned.
A majority of the impacted servers are positioned in China, adopted by way of Hong Kong, Netherlands, Japan, the U.S., Germany, South Africa, and Sweden.
BYOVD and Different Undermine Safety Mechanisms
BYOVD is an an increasing number of widespread method during which a danger actor brings a known-vulnerable signed driving force, quite a bit it into the kernel, and exploits it to accomplish privileged movements, incessantly with an purpose to disarm safety processes and make allowance them to function stealthily.
“Drivers run at ring 0, essentially the most privileged degree of the working device,” Israeli cybersecurity company Cymulate notes. “This grants them direct get entry to to essential reminiscence, CPU, I/O operations, and different elementary assets. Relating to BYOVD, the assault is designed to load a weak driving force to additional the assault.”
Even supposing Microsoft has deployed the Prone Motive force Blocklist by way of default beginning in Home windows 11 22H2, the checklist is best up to date best a couple of times a yr, necessitating that customers manually replace it periodically for optimum coverage.
The precise scope of the marketing campaign stays unknown and it is these days now not transparent who’s at the back of it. On the other hand, the extraordinary sophistication at the back of what seems to be a simple illicit cryptocurrency mining assault bears understand.

The disclosure additionally follows the invention of a singular method referred to as EDRaser that takes benefit of flaws in Microsoft Defender (CVE-2023-24860 and CVE-2023-36010) to remotely delete get entry to logs, Home windows tournament logs, databases, and different recordsdata.
The problem, which additionally affects Kaspersky, stems from the truth that each the safety methods use byte signatures to hit upon malware, thus permitting a danger actor to implant malware signatures into official recordsdata and idiot the gear into pondering that they’re malicious, SafeBreach mentioned.
The cybersecurity corporate has one after the other exposed an inventive exploit to get round safety protections introduced by way of Palo Alto Networks Cortex XDR and weaponize it to deploy a opposite shell and ransomware, successfully repurposing it right into a rogue offensive instrument.

At its core, the bypass makes it imaginable to load a weak driving force (“rtcore64.sys”) by way of a BYOVD assault and tamper with the technique to save you a valid administrator from disposing of the instrument and in the long run insert malicious code into one among its processes, granting the danger actor prime privileges whilst closing undetected and chronic.
“The common sense at the back of the detection processes of a safety product will have to be intently guarded,” safety researcher Shmuel Cohen mentioned closing month. “By way of giving attackers get entry to to this delicate detection common sense by way of the answer’s content material recordsdata, they’re a lot more most probably so that you could engineer some way round it.”
Some other novel way is HookChain, which, as Brazilian safety researcher Helvio Carvalho Junior, comes to combining IAT hooking, dynamic device provider numbers (SSN) answer, and oblique device calls to flee tracking and management mechanisms applied by way of safety instrument within the consumer mode, in particular within the NTDLL.dll library.
“HookChain is in a position to redirecting the execution float of all primary Home windows subsystems, similar to kernel32.dll, kernelbase.dll, and user32.dll,” Carvalho Junior mentioned in a newly printed paper.
“Because of this, as soon as deployed, HookChain guarantees that each one API calls throughout the context of an utility are performed transparently, totally warding off detection by way of [Endpoint detection and response software].”
