Proof-of-concept exploit code has been launched for a top-severity safety vulnerability in Progress Flowmon, a software for monitoring community efficiency and visibility.
Progress Flowmon combines efficiency monitoring, diagnostics, and community detection and response options. It’s utilized by greater than 1,500 corporations around the globe, together with SEGA, KIA, and TDK, Volkswagen, Orange, and Tietoevry.
The safety concern has the utmost severity rating of 10/10 and was found by researchers at Rhino Safety Labs. It’s at the moment tracked as CVE-2024-2389.
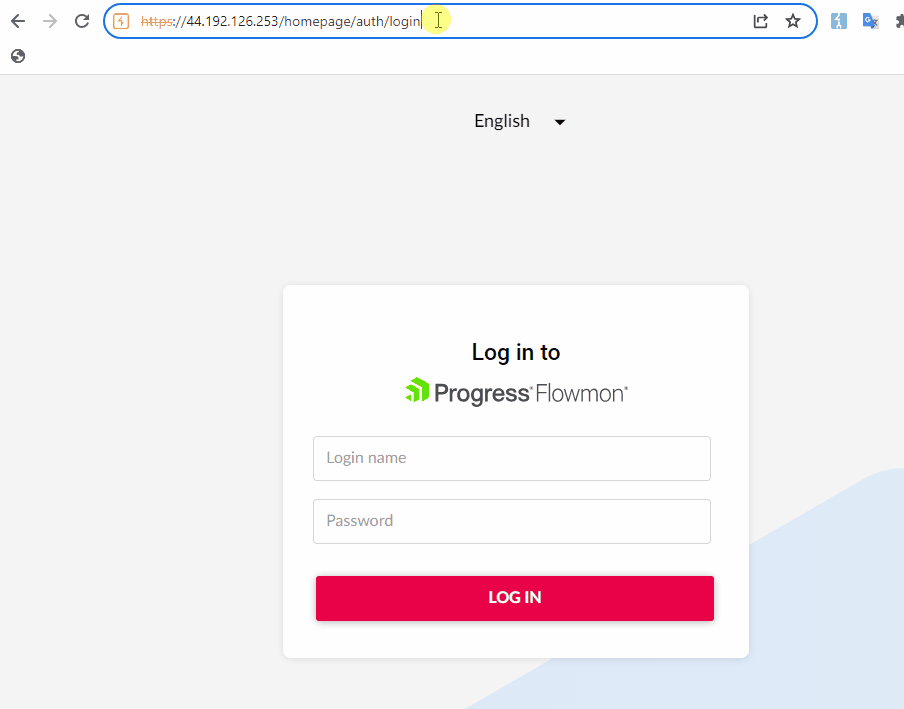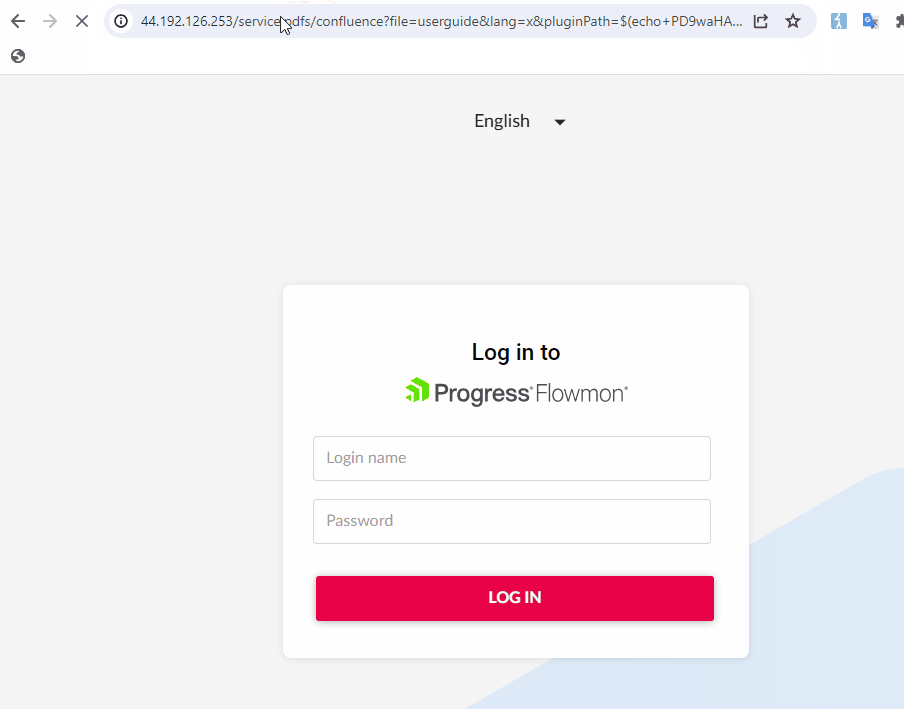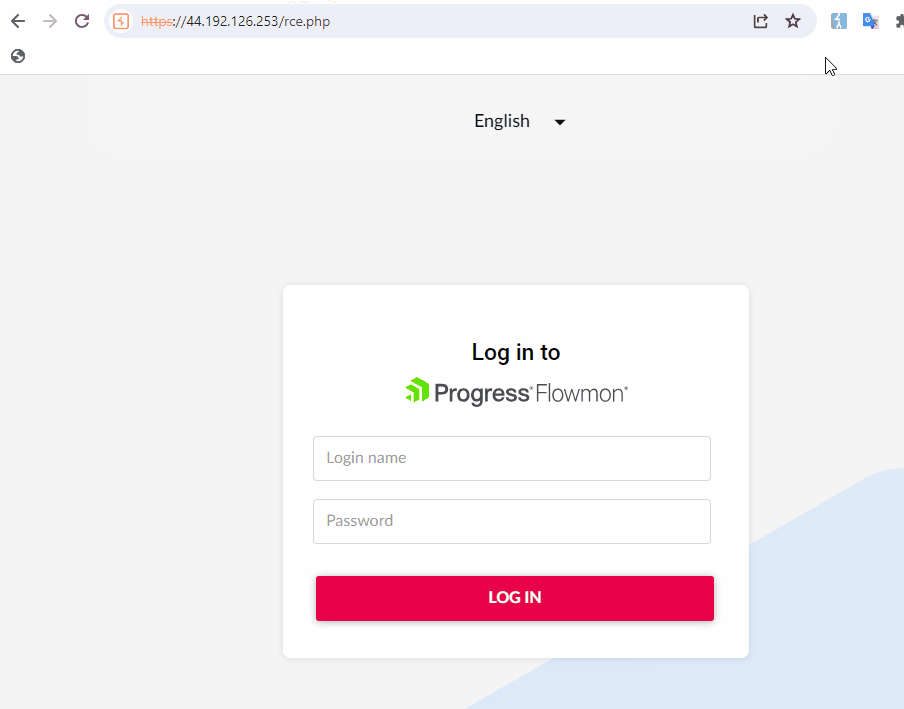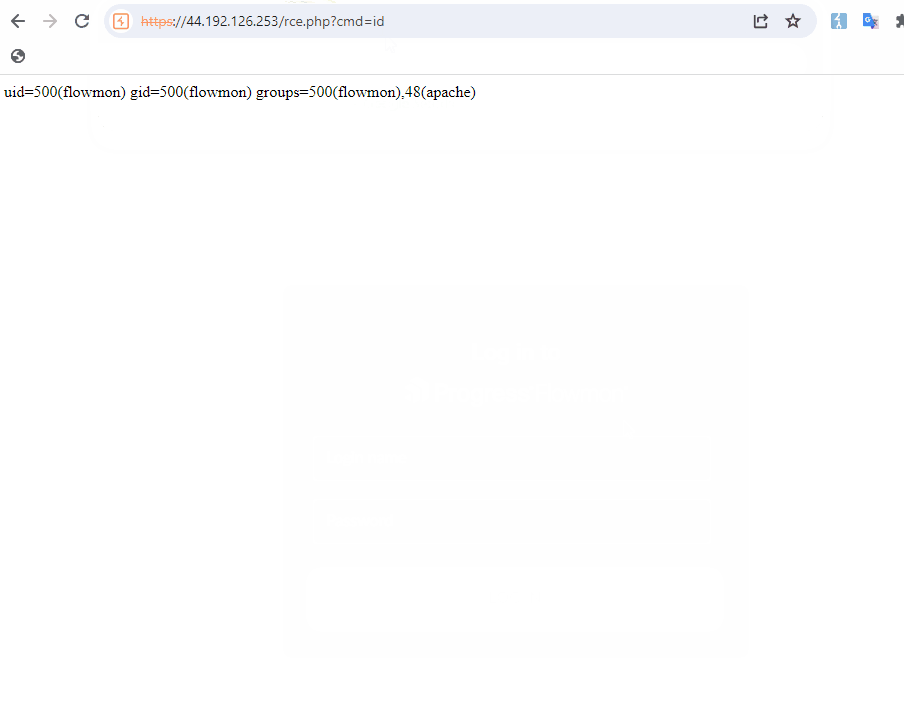
An attacker can exploiting the vulnerability can use a specifically crafted API request to achieve distant, unauthenticated entry to the Flowmon net interface and execute arbitrary system instructions.
Flowon developer Progress Software program first alerted in regards to the flaw on April 4, warning that it impacts variations of the product v12.x and v11.x. The corporate urged system admins to improve to the most recent releases, v12.3.4 and 11.1.14.
The safety replace was launched to all Flowmon clients both mechanically by the ‘Automated package deal obtain’ system or manually from the seller’s obtain middle. Progress additionally advisable upgrading all Flowmon modules afterwards.
Exploit code out there
In a report at present, Rhino Safety Labs launched technical particulars for the vulnerability together with a demo displaying how an attacker may exploit the difficulty to plant a webshell and escalate privileges to root.
The researchers clarify that they had been in a position to inject instructions by manipulating the ‘pluginPath’ or ‘file parameters’ to embed malicious instructions. Utilizing the command substitution syntax , e.g. $(…), the researchers may obtain arbitrary command execution.
“The command executes blindly so it isn’t doable to see the output of the executed command, however it’s doable to put in writing a webshell to /var/www/shtml/,” the researchers clarify.
Rhino Safety
It’s value noting that in an alert about two weeks in the past Italy’s CSIRT warned that an exploit had already turn into out there. Certainly, BleepingComputer discovered {that a} safety researcher had revealed on April 10 a sound PoC for CVE-2024-2389 on X.
Flowmon servers uncovered
The variety of Flowmon cases uncovered on the general public net seems to differ significantly relying on the search engine.
At publishing time, a look on the Fofa search engine for community belongings reveals that there are about 500 Flowmon servers uncovered on-line. Shodan and Hunter engines like google see lower than 100 cases.
On April 19, Progress Software program in a safety bulletin assured its clients that there have been no experiences of energetic exploitation for CVE-2024-2389. Nonetheless, addressing the difficulty by upgrading to a protected model as quickly as doable is vital.
