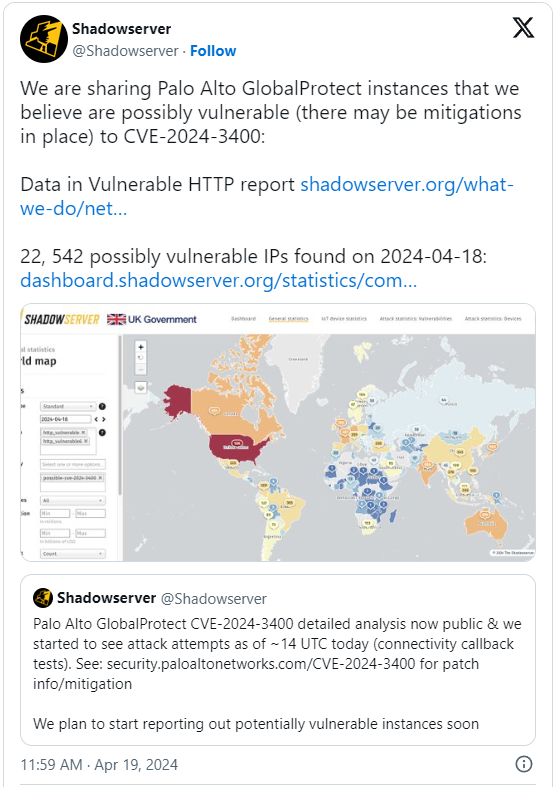
Roughly 22,500 uncovered Palo Alto GlobalProtect firewall units are possible weak to the CVE-2024-3400 flaw, a essential command injection vulnerability that has been actively exploited in assaults since no less than March 26, 2024.
CVE-2024-3400 is a essential vulnerability impacting particular Palo Alto Networks’ PAN-OS variations in the GlobalProtect characteristic that enables unauthenticated attackers to execute instructions with root privileges utilizing command injection triggered by arbitrary file creation.
The flaw was disclosed by Palo Alto Networks on April 12, with the safety advisory urging system directors to use supplied mitigations instantly till a patch was made out there.
Relying on the PAN-OS model, patches have been made out there between April 14 and 18, 2024, so the publicity to post-disclosure dangers lasted two to 6 days. It was later revealed that Palo Alto’s mitigation of disabling telemetry wouldn’t shield units and that the one resolution was to use the safety patches.
Volexity researchers who first found the exploitation revealed that state-backed risk actors tracked as ‘UTA0218’ exploited the flaw to contaminate techniques with a customized backdoor named ‘Upstyle.’
Earlier this week, researchers shared technical particulars and a proof-of-concept exploit for CVE-2024-3400, demonstrating how simply unauthenticated attackers may execute instructions as root on unpatched endpoints.
The general public availability of the exploit has allowed quite a few risk actors to conduct their personal assaults, leaving system directors with no margins to delay patching.
Greynoise’s scanners confirmed this elevated exploitation, displaying bigger numbers of distinctive IP addresses making an attempt to use the CVE-2024-3400 flaw.
Regardless of the urgency of the state of affairs, the ShadowServer Basis risk monitoring service says there are nonetheless roughly 22,500 cases which might be “presumably weak” as of April 18, 2024.
Many of the units are positioned in the USA (9,620), adopted by Japan (960), India (890), Germany (790), the UK (780), Canada (620), Australia (580), and France (500).
Earlier this week, Shadow Server reported seeing over 156,000 PAN-OS firewall cases uncovered on the web with out discerning what number of of these could be weak to assaults.
Final Friday, risk researcher Yutaka Sejiyama performed his personal scans and reported observing 82,000 firewalls, which he claimed have been weak to CVE-2024-34000.
If the researcher’s estimations have been correct, roughly 73% of all uncovered PAN-OS techniques have been patched inside per week.
Those that have not taken any motion are suggested to observe the recommended actions within the Palo Alto safety advisory, which has been up to date a number of instances since final week with new info and directions on attempting to find suspicious exercise.