A vulnerability tracked as CVE-2024-31497 in PuTTY 0.68 by 0.80 may probably permit attackers with entry to 60 cryptographic signatures to get well the non-public key used for his or her era.
PuTTY is a well-liked open-source terminal emulator, serial console, and community file switch utility that helps SSH (Safe Shell), Telnet, SCP (Safe Copy Protocol), and SFTP (SSH File Switch Protocol).
System directors and builders predominantly use the software program to remotely entry and handle servers and different networked gadgets over SSH from a Home windows-based consumer.
The vulnerability tracked as CVE-2024-31497 was found by Fabian Bäumer and Marcus Brinkmann of the Ruhr College Bochum and is brought on by how PuTTY generates ECDSA nonces (momentary distinctive cryptographic numbers) for the NIST P-521 curve used for SSH authentication.
Particularly, there is a bias as a result of PuTYY’s use of a deterministic technique to generate these numbers to compensate for the dearth of a sturdy cryptographic random quantity generator on particular Home windows variations.
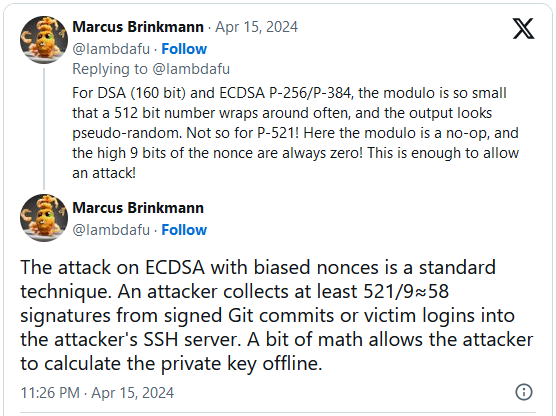
“PuTTY’s method labored by making a SHA-512 hash after which decreasing it mod q, the place q is the order of the group used within the DSA system. For integer DSA (for which PuTTY’s method was initially developed), q is about 160 bits; for elliptic-curve DSA (which got here later), it has about the identical variety of bits because the curve modulus, so 256 or 384 or 521 bits for the NIST curves.”
“In all of these instances besides P521, the bias launched by decreasing a 512-bit quantity mod q is negligible. However within the case of P521, the place q has 521 bits (i.e. greater than 512), decreasing a 512-bit quantity mod q has no impact in any respect – you get a worth of okay whose high 9 bits are at all times zero.” – PuTTY safety advisory.
The primary repercussion of recovering the non-public secret is that it permits unauthorized entry to SSH servers or signal commits because the developer.
Exploiting CVE-2024-31497
A digital signature is created utilizing a consumer’s non-public key and verified by the corresponding public key on the server, making certain the consumer’s id and the communication’s safety.
Brinkmann defined on X that attackers require 58 signatures to calculate a goal’s non-public key, which they will purchase both by gathering them from logins to an SSH server they management or is compromised, or from signed Git commits.
Accumulating signatures from an SSH server will not be as important as it could imply the server itself is already compromised, and thus, the risk actor has broad entry to the working system.
Nevertheless, Bäumer advised BleepingComputer that the second technique of harvesting signatures from public commits is much extra sensible for attackers.
There are cases the place this vulnerability could be exploited with out the necessity to compromise a server prematurely.
One such case is using SSH keys for signing Git commits. A standard setup includes utilizing Pageant, the ssh-agent of PuTTY, domestically and forwarding the agent to a improvement host.
Right here, you configure Git to make use of OpenSSH to signal Git commits with the SSH key supplied by Pageant. The signature is then generated by Pageant, making it inclined to personal key restoration.
That is significantly regarding as git signatures could also be publicly accessible, for instance, if the commit is pushed to a public repository on GitHub.
❖ Fabian Bäumer
Flaw mounted, different software program impacted
The builders mounted the vulnerability in PuTTY model 0.81, which abandons the earlier k-generation technique and switches to the RFC 6979 method for all DSA and ECDSA keys.
Nevertheless, it’s famous that any P521 non-public keys generated utilizing the susceptible model of the device needs to be thought-about unsafe and changed by new, safe keys.
The next software program that makes use of the susceptible PuTTY is confirmed as impacted:
- FileZilla 3.24.1 – 3.66.5 (mounted in 3.67.0)
- WinSCP 5.9.5 – 6.3.2 (mounted in 6.3.3)
- TortoiseGit 2.4.0.2 – 2.15.0 (mounted in 2.15.0.1)
- TortoiseSVN 1.10.0 – 1.14.6 (mitigation attainable by configuring TortoiseSVN to make use of Plink from the most recent PuTTY 0.81 launch)
There are seemingly extra software program instruments impacted by CVE-2024-31497, relying on which PuTTY model they incorporate. Due to this fact, customers are suggested to verify their instruments and take preventive motion as wanted.