Newly found HTTP/2 protocol vulnerabilities known as “CONTINUATION Flood” can result in denial of service (DoS) assaults, crashing net servers with a single TCP connection in some implementations.
HTTP/2 is an replace to the HTTP protocol standardized in 2015, designed to enhance net efficiency by introducing binary framing for environment friendly information transmission, multiplexing to permit a number of requests and responses over a single connection, and header compression to scale back overhead
The brand new CONTINUATION Flood vulnerabilities have been found by researcher Barket Nowotarski, who says that it pertains to using HTTP/2 CONTINUATION frames, which aren’t correctly restricted or checked in lots of implementations of the protocol.
HTTP/2 messages embody header and trailer sections serialized into blocks. These blocks could be fragmented throughout a number of frames for transmission, and the CONTINUATION frames are used for stitching the stream.
The omission of correct body checks in lots of implementations permits risk actors to doubtlessly ship a particularly lengthy string of frames by merely not setting the ‘END_HEADERS’ flag, resulting in server outages resulting from out-of-memory crashes or CPU useful resource exhaustion as these frames are processed.
The researcher warned that out of reminiscence situations could lead on to server crashes utilizing a single HTTP/2 TCP connection in some implementations.
“Out of Reminiscence are in all probability essentially the most boring but extreme circumstances. There’s nothing particular about it: no unusual logic, no attention-grabbing race situation and so forth,” Nowotarski explains.
“The implementations that enable OOM merely didn’t restrict the scale of headers listing constructed utilizing CONTINUATION frames.”
“Implementations with out header timeout required only a single HTTP/2 connection to crash the server.”
An alert from the CERT Coordination Middle (CERT-CC) revealed right this moment lists a number of CVE IDs equivalent to completely different HTTP/2 implementations susceptible to those assaults.
These implementations enable various ranges of denial of service assaults, together with reminiscence leaks, reminiscence consumption, and CPU exhaustion, as described under:
- CVE-2024-27983: Impacts Node.js HTTP/2 server. Sending a number of HTTP/2 frames may cause a reminiscence leak resulting from a race situation, resulting in a possible DoS.
- CVE-2024-27919: Impacts Envoy’s oghttp codec. Limitless reminiscence consumption resulting from not resetting a request when header map limits are exceeded.
- CVE-2024-2758: Pertains to Tempesta FW. Its charge limits usually are not successfully stopping empty CONTINUATION frames assaults, doubtlessly permitting DoS.
- CVE-2024-2653: Impacts amphp/http. It collects CONTINUATION frames in an unbounded buffer, risking an OOM crash if the header dimension restrict is exceeded.
- CVE-2023-45288: Impacts Go’s web/http and web/http2 packages. Permits an attacker to ship an arbitrarily massive set of headers, inflicting extreme CPU consumption.
- CVE-2024-28182: Entails an implementation utilizing nghttp2 library, which continues to obtain CONTINUATION frames, resulting in a DoS with out correct stream reset callback.
- CVE-2024-27316: Impacts Apache Httpd. Steady stream of CONTINUATION frames with out the END_HEADERS flag set could be despatched, improperly terminating requests.
- CVE-2024-31309: Impacts Apache Visitors Server. HTTP/2 CONTINUATION DoS assault may cause extreme useful resource consumption on the server.
- CVE-2024-30255: Impacts Envoy variations 1.29.2 or earlier. Susceptible to CPU exhaustion resulting from a flood of CONTINUATION frames, consuming vital server assets.
Extreme affect
To date, based on CERT-CC, distributors and HTTP/2 libraries who’ve confirmed they’re impacted by at the very least one of many above CVEs are Crimson Hat, SUSE Linux, Arista Networks, the Apache HTTP Server Venture, nghttp2, Node.js, AMPHP, and the Go Programming Language.
Nowotarski says the issue is extra extreme than the ‘HTTP/2 Speedy Reset’ assault revealed final October by main cloud service suppliers, which has been beneath lively exploitation since August 2023.
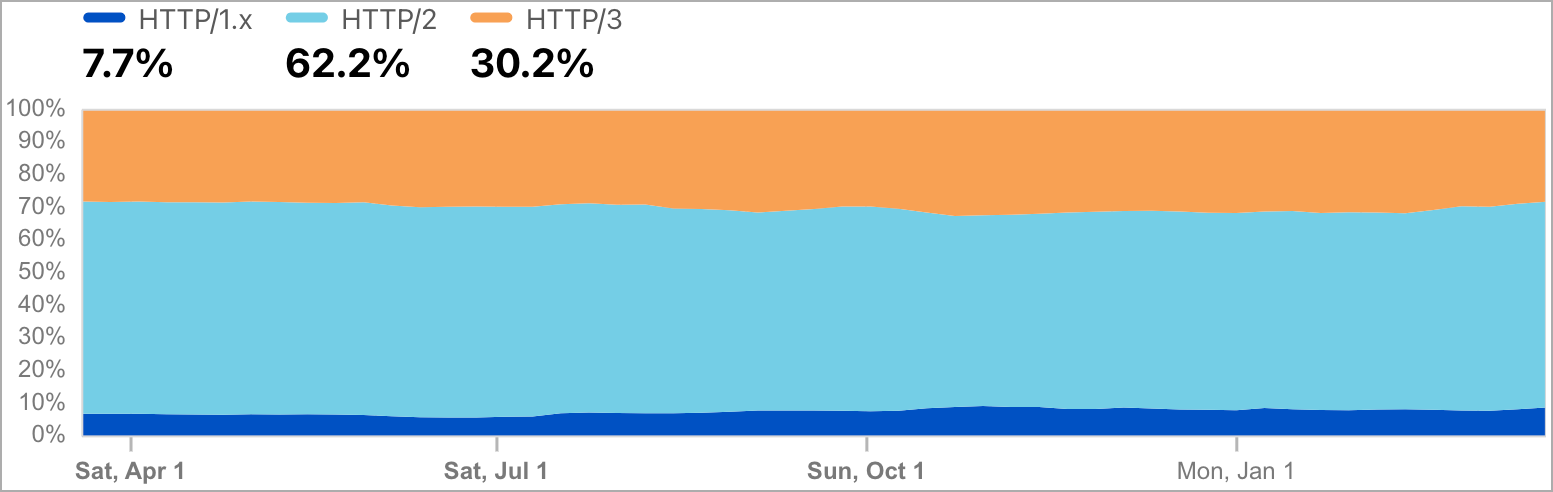
“Provided that Cloudflare Radar estimates HTTP visitors information above 70% of all web switch and significance of affected initiatives I imagine that we will assume that enormous a part of web was affected by an easy-to-exploit vulnerability: in lots of circumstances only a single TCP connection was sufficient to crash the server, ” warned Nowotarski.
Additionally, the researcher warns that the issue could be complicated for server directors to debug and mitigate with out correct HTTP/2 data.
That is as a result of the malicious requests would not be seen within the entry logs if superior body analytics is not enabled on the server, which usually is not.
As risk actors generally monitor for newly found DDoS strategies to make use of of their stresser providers and assaults, it’s essential to improve impacted servers and libraries earlier than the vulnerabilities are actively exploited.
