Cybersecurity researchers have disclosed that the LightSpy spy ware allegedly concentrated on Apple iOS customers is in reality a up to now undocumented macOS variant of the implant.
The findings come from each Huntress Labs and ThreatFabric, which one at a time analyzed the artifacts related to the cross-platform malware framework that most probably possesses features to contaminate Android, iOS, Home windows, macOS, Linux, and routers from NETGEAR, Linksys, and ASUS.
“The Danger actor staff used two publicly to be had exploits (CVE-2018-4233, CVE-2018-4404) to ship implants for macOS,” ThreatFabric mentioned in a file revealed ultimate week. “A part of the CVE-2018-4404 exploit is most probably borrowed from the Metasploit framework. macOS model 10 used to be focused the use of the ones exploits.”
LightSpy used to be first publicly reported in 2020, even if next studies from Lookout and the Dutch cell safety company have printed imaginable connections between the spy ware and an Android surveillance instrument referred to as DragonEgg.
Previous this April, BlackBerry disclosed what it mentioned used to be a “renewed” cyber espionage marketing campaign concentrated on customers in South Asia to ship an iOS model of LightSpy. However this has now been discovered to be a a lot more subtle macOS model that employs a plugin-based machine to reap more than a few forms of knowledge.

“Additionally it is value noting that whilst this pattern used to be uploaded to VirusTotal just lately from India, this is not a specifically sturdy indicator of an lively marketing campaign, nor concentrated on inside the area,” Huntress researchers Stuart Ashenbrenner and Alden Schmidt mentioned.
“It is a contributing issue, however with out extra concrete proof or visibility into supply mechanisms, it will have to be desirous about a heavy grain of salt.”
ThreatFabric’s research has printed that the macOS taste has been lively within the wild since no less than January 2024, however confined to with reference to 20 gadgets, a majority of which might be mentioned to be take a look at gadgets.
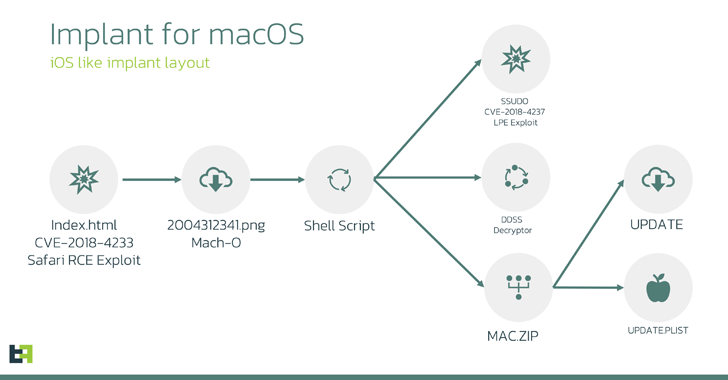
The assault chain starts with the exploitation of CVE-2018-4233, a Safari WebKit flaw, by the use of rogue HTML pages to cause code execution, resulting in the supply of a 64-bit MachO binary that masquerades as a PNG symbol document.

The binary is essentially designed to extract and release a shell script that, in flip, fetches 3 further payloads: A privilege escalation exploit, an encryption/decryption software, and a ZIP archive.
The script therefore extracts the contents of the ZIP archive — replace and replace.plist — and assigns root privileges to either one of them. The ideas assets checklist (plist) document is used to arrange endurance for the opposite document such that it is introduced each and every time after a machine restart.
The “replace” document (aka macircloader) acts as a loader for the LightSpy Core element, permitting the latter to determine touch with a command-and-control (C2) server and retrieve instructions in addition to obtain plugins.
The macOS model comes with make stronger for 10 other plugins to seize audio from the microphone, take footage, file display screen job, harvest and delete recordsdata, execute shell instructions, clutch the checklist of put in programs and working processes, and extract knowledge from internet browsers (Safari and Google Chrome) and iCloud Keychain.
Two different plugins additional make it imaginable to seize details about the entire different gadgets which can be attached to the similar community because the sufferer, the checklist of Wi-Fi networks the tool has attached to, and information about the within sight Wi-Fi networks.

“The Core serves as a command dispatcher and extra plugins prolong the capability,” ThreatFabric famous. “Each the Core and plugins may well be up to date dynamically through a command from C2.”
The cybersecurity company mentioned it used to be ready to discover a misconfiguration that made it imaginable to realize get right of entry to to the C2 panel, together with a far flung management platform, which incorporates details about the sufferers and the related knowledge.
“Irrespective of the focused platform, the danger actor staff all for intercepting sufferer communications, similar to messenger conversations and voice recordings,” the corporate mentioned. “For macOS, a specialised plugin used to be designed for community discovery, aiming to spot gadgets in proximity to the sufferer.”

The improvement comes as Android gadgets were focused with recognized banking trojans similar to BankBot and SpyNote in assaults geared toward cell banking app customers in Uzbekistan and Brazil, in addition to through impersonating a Mexico telecom carrier supplier to contaminate customers in Latin The us and the Caribbean.
It additionally comes as a file from Get admission to Now and the Citizen Lab exposed proof of Pegasus spy ware assaults concentrated on seven Russian and Belarusian-speaking opposition activists and impartial media in Latvia, Lithuania, and Poland.
“Using Pegasus spy ware to focus on Russian- and Belarusian-speaking newshounds and activists dates again till no less than 2020, with extra assaults following Russia’s full-scale invasion of Ukraine in February 2022,” Get admission to Now mentioned, including “a unmarried Pegasus spy ware operator could also be in the back of the concentrated on of no less than 3 of the sufferers and perhaps all 5.”
