An in depth safety audit of QNAP QTS, the running device for the corporate’s NAS merchandise, has exposed fifteen vulnerabilities of various severity, with 11 closing unfixed.
Amongst them is CVE-2024-27130, an unpatched stack buffer overflow vulnerability within the ‘No_Support_ACL’ serve as of ‘proportion.cgi,’ which might permit an attacker to accomplish faraway code execution when particular necessities are met.
The seller replied to the vulnerability reviews submitted between December 12, 2023, and January 23, 2024, with more than one delays and has mounted best 4 of the fifteen flaws.
The vulnerabilities had been came upon via WatchTowr Labs, who revealed the whole main points in their findings and an evidence of idea (PoC) exploit for CVE-2024-27130 on Friday.
The QTS vulnerabilities
The issues exposed via WatchTowr analysts are basically associated with code execution, buffer overflows, reminiscence corruption, authentication bypass, and XSS problems, impacting the protection of Community Hooked up Garage (NAS) gadgets throughout other deployment environments.
WatchTowr lists a complete of fifteen flaws, summarized as follows:
- CVE-2023-50361: Unsafe use of sprintf in getQpkgDir invoked from userConfig.cgi.
- CVE-2023-50362: Unsafe use of SQLite purposes out there by means of parameter addPersonalSmtp to userConfig.cgi.
- CVE-2023-50363: Lacking authentication lets in two-factor authentication to be disabled for arbitrary customers.
- CVE-2023-50364: Heap overflow by means of lengthy listing identify when document checklist is seen via get_dirs serve as of privWizard.cgi.
- CVE-2024-21902: Lacking authentication lets in all customers to view or transparent device logs and carry out further movements.
- CVE-2024-27127: A double-free in utilRequest.cgi by means of the delete_share serve as.
- CVE-2024-27128: Stack overflow in check_email serve as, reachable by means of the share_file and send_share_mail movements of utilRequest.cgi.
- CVE-2024-27129: Unsafe use of strcpy in get_tree serve as of utilRequest.cgi.
- CVE-2024-27130: Unsafe use of strcpy in No_Support_ACL out there via get_file_size serve as of proportion.cgi.
- CVE-2024-27131: Log spoofing by means of x-forwarded-for lets in customers to reason downloads to be recorded as asked from arbitrary supply places.
- WT-2023-0050: Below prolonged embargo because of an abruptly complicated factor.
- WT-2024-0004: Saved XSS by means of faraway syslog messages.
- WT-2024-0005: Saved XSS by means of faraway instrument discovery.
- WT-2024-0006: Loss of rate-limiting on authentication API.
- WT-2024-00XX: Below 90-day embargo as consistent with VDP.
The above insects have an effect on QTS, the NAS running device on QNAP gadgets, QuTScloud, the VM-optimized model of QTS, and QTS hero, a specialised model excited about top efficiency.
QNAP has addressed CVE-2023-50361 thru CVE-2023-50364 in a safety replace launched in April 2024, in variations QTS 5.1.6.2722 construct 20240402 and later, and QuTS hero h5.1.6.2734 construct 20240414 and later.
Alternatively, the entire different vulnerabilities came upon via WatchTowr stay unaddressed.
PoC for zero-day RCE
The QNAP CVE-2024-27130 vulnerability is brought about via the unsafe use of the ‘strcpy’ serve as within the No_Support_ACL serve as. This serve as is used by the get_file_size request within the proportion.cgi script, used when sharing media with exterior customers.
An attacker can craft a malicious request with a specifically crafted ‘identify’ parameter, inflicting the buffer overflow resulting in faraway code execution.
To milk CVE-2024-27130, the attacker wishes a sound ‘ssid’ parameter, which is generated when a NAS person stocks a document from their QNAP instrument.
This parameter is incorporated within the URL of the ‘proportion’ hyperlink created on a tool, so an attacker could be required to use some social engineering to realize get admission to to it. Alternatively, BleepingComputer discovered that customers now and again proportion those hyperlinks on-line, letting them be listed and retrieved from a easy Google seek.
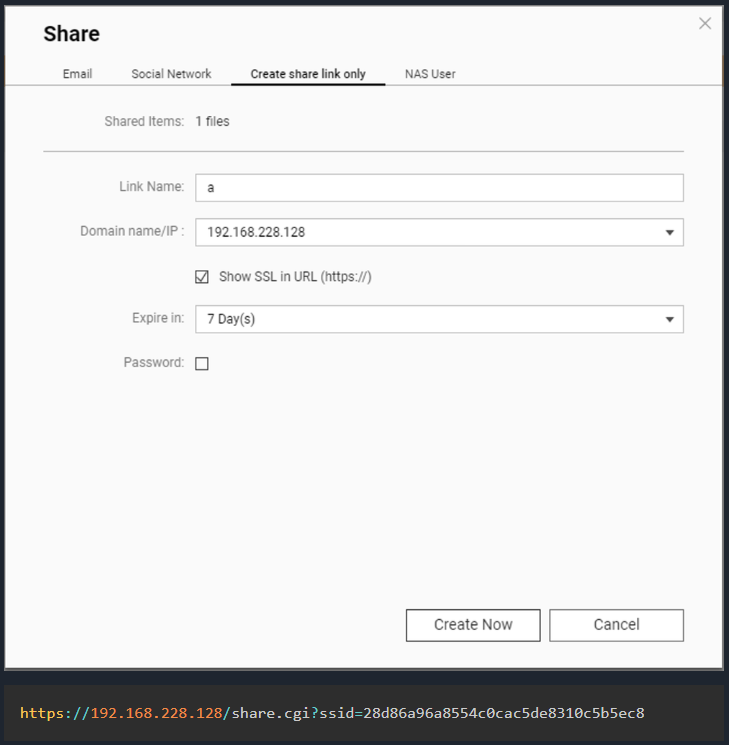
Supply: WatchTowr
In abstract, CVE-2024-27130 is not simple to milk, but the SSID prerequisite can also be met for made up our minds actors.
WatchTowr revealed an exploit on GitHub, wherein they display the right way to craft a payload that creates a ‘watchtowr’ account to a QNAP instrument and provides them to the sudoers for increased privileges.
BleepingComputer has contacted QNAP for a observation at the disclosed flaws, however a remark wasn’t in an instant to be had.
